Affiliate links on Android Authority may earn us a commission. Learn more.
How to encrypt your Android device
There’s little doubt that keeping your personal data secure these days is pretty important, so it’s fortunate that Android gives you the encryption tools you need to secure your device right out of the box. If you have been wondering how to get started with securing your digital data, this guide will walk you through how to encrypt your Android device.
QUICK ANSWER
Newer Android phones are encrypted by default as long as you set up a lockscreen. In other words, simply set a pattern, PIN, or password to take advantage of Android's built-in encryption. If you don’t set either of these, an attacker can simply gain access to your device, without even having to break through Android's encryption.
If you need to encrypt your microSD card, you’ll have to manually do so under Settings > Security. However, this feature may not be present on every Android device.
JUMP TO KEY SECTIONS
How to encrypt an Android phone: Set a screen lock

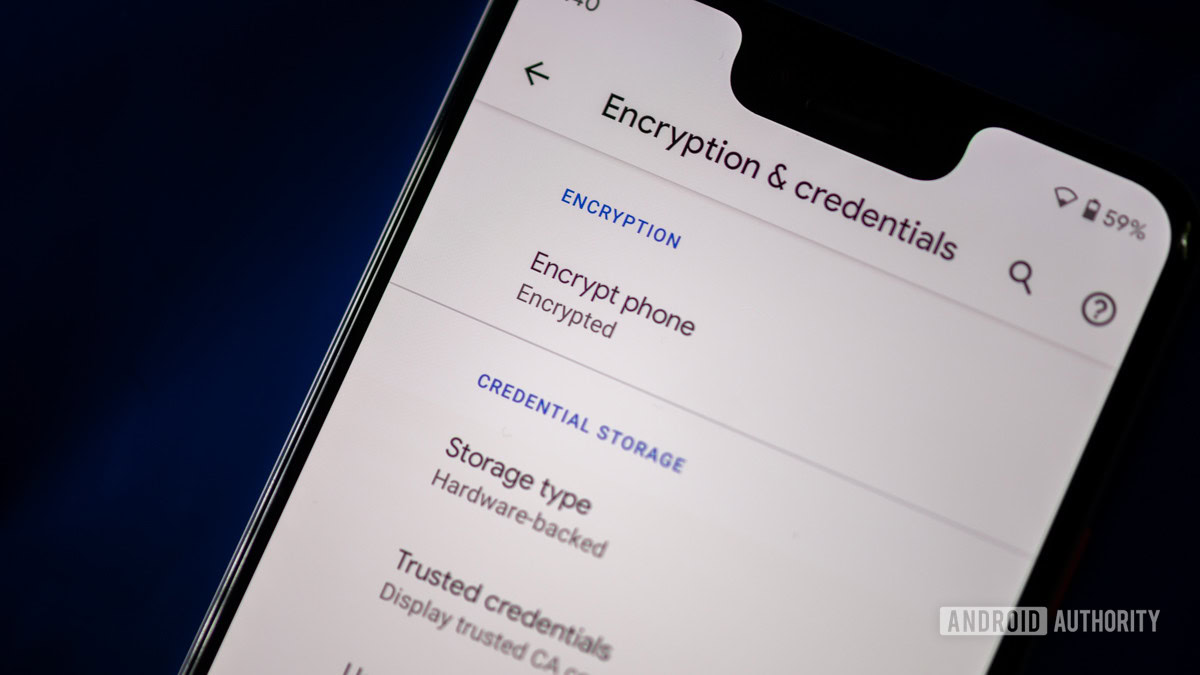
Virtually all Android devices on the market now come with encryption enabled by default. This is because Google required manufacturers to enable full-disk encryption starting with Android 6.0 Marshmallow, which debuted all the way back in 2015. With the release of Android 10 in 2019, that requirement was revised to the newer file-based encryption instead. The latter makes encryption a whole lot more painless from an end-user perspective.
Rather than locking down the entire device, file-based encryption uses different keys for non-sensitive and sensitive files. And thanks to Direct Boot, another relatively recent Android feature, encrypted devices can start up with core functionality like alarms, voice calls, and SMS enabled. Sensitive data like user data and third-party apps, meanwhile, stay encrypted until you unlock the device.
If you use a screen lock on your Android smartphone, full-disk encryption is enabled by default.
In summary, a new Android device will not prompt you to enable encryption when you set it up nor will you find a manual toggle in the Settings app. All you need to do is set a screen lock of some kind. Fortunately, this is a rather simple process. Head on over to Settings > Lockscreen and Security and pick a pattern, numbered PIN, or mixed password for your lock screen.
How to encrypt text messages on Android
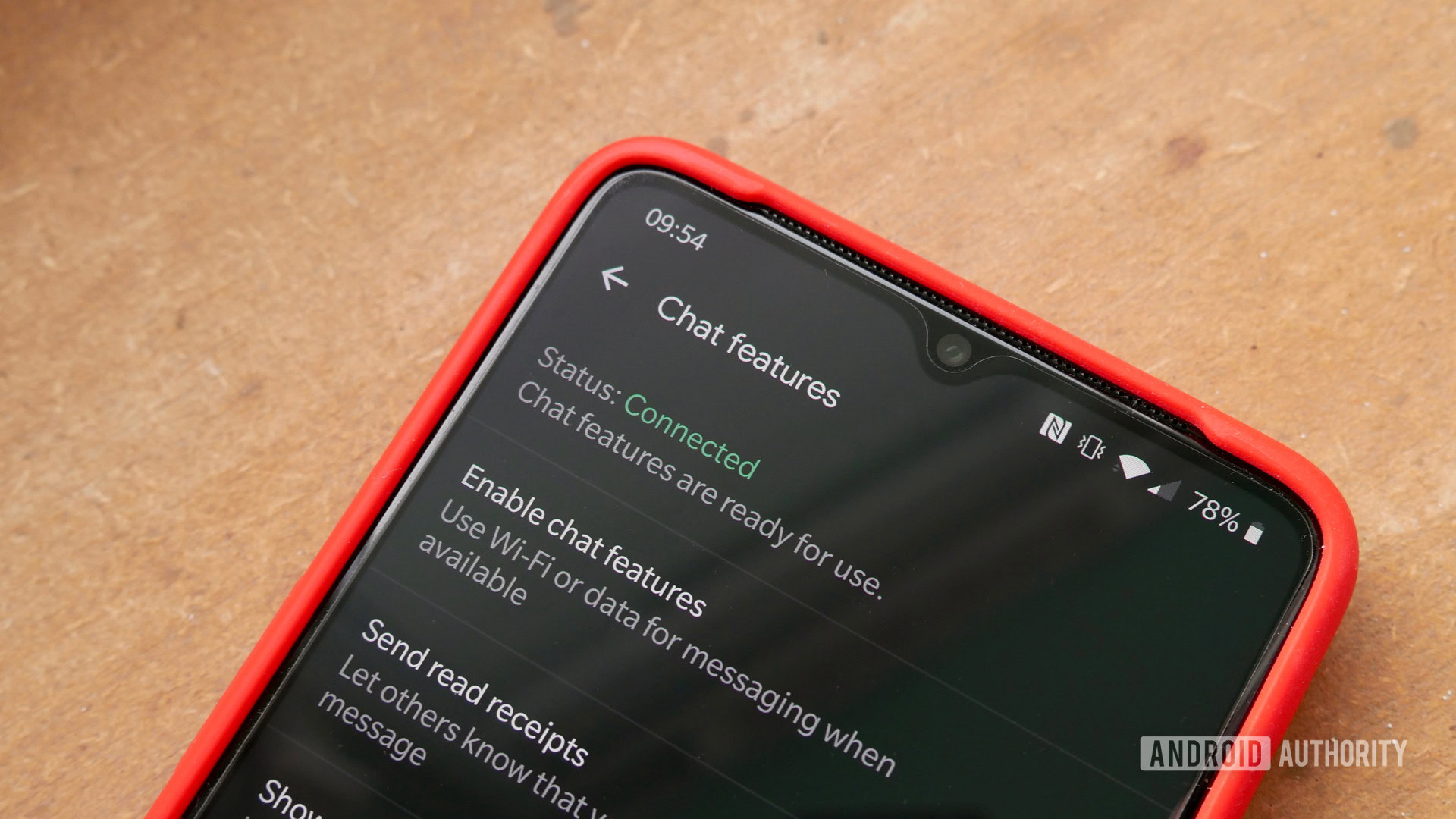
While your Android phone only needs a lockscreen password or PIN to stay encrypted, that’s not true for other apps on your device. SMS or text messages, for example, do not get any encryption whatsoever by default. Luckily, there are several alternatives to choose from if you’d like a more secure messaging experience:
- Switch to RCS: If your contacts use Android as well, consider switching to Rich Communication Services (RCS) instead of SMS. You can think of RCS as a more modern form of SMS with end-to-end encryption built-in. Best of all, you don’t need to install an app to use it on most phones. The Google Messages app supports RCS right out of the box.
- Use an encrypted chat app: Looking for the most secure solution? Look no further than Signal, the app that prides itself on its robust encryption. In fact, even some of the most popular apps like WhatsApp use Signal’s encryption protocol under the hood. The only downside is that you’ll have to ask your contacts to download Signal (or WhatsApp) on their devices as well.
Encrypt a microSD card on Android

It’s worth noting that encryption is not enabled by default on external storage like microSD cards. This is because the encryption key lives on the Android device itself, making it impossible to read the microSD card’s data anywhere else or even after a factory reset. Most users don’t anticipate this behavior and expect to be able to move microSD cards between devices freely.
Luckily, many Android OEMs offer a way to encrypt the contents of your microSD card — provided you’re willing to put up with the above limitations.
The exact steps may vary depending on your device’s Android flavor, but generally speaking, you’ll find the option under Settings > Security. Keep in mind that this is a slow process, so you may have to set your device aside for a while. The exact duration depends on the amount of data already present on the microSD card.
Once again, you can only read an encrypted microSD card on the original device. If you intend on performing a factory reset or upgrading your device, remember to manually decrypt it first.
Next steps: How to encrypt photos and files on Android
If your objective is simply to encrypt specific files or photos on your Android device, you’ll have to use a third-party app. Here are a few recommendations for encryption apps:
DroidFS
DroidFS is a free and open-source Android app that allows you to create and browse encrypted virtual volumes. It uses gocryptfs as its underlying encryption scheme, which means that you can access these vaults on any Linux desktop too. The app offers a full-fledged internal file browser, media viewer, and even an internal camera to directly capture and encrypt photos.
You’ll have to use the open-source app store F-Droid to install DroidFS since it isn’t available on the Play Store. Alternatively, you can find more information within the project’s GitHub repository.
Photok
If you specifically need to encrypt images, Photok fits the bill perfectly. It offers a photo gallery-esque view of your files instead of an all-purpose file browser. The app is also open-source and relies on the AES-256 encryption standard. While not as feature-rich as DroidFS, it does offer the ability to create backups.
You can download Photok from the Play Store or the developer’s GitHub repository.
Google Photos
After realizing the demand for encrypted media, Google added a locked folder to its Photos app across all platforms. You can also choose to back up encrypted media to the cloud and access it on other devices. However, it’s worth noting that this approach isn’t as secure since your Google password acts as a single point of failure. For that reason alone, you should turn off locked folder backups.
FAQs
No, you don’t need to install anything to encrypt your Android device. Simply enable a screen lock like a PIN, pattern, or password and your phone’s contents will be automatically encrypted for you.
To encrypt a modern Android phone, simply set up a screen lock like a pattern or PIN.
No, an encrypted Android device cannot be hacked. However, if you don’t install the latest security updates, a future vulnerability may allow hackers to bypass the encryption.