Affiliate links on Android Authority may earn us a commission. Learn more.
⚡ Welcome again to The Weekly Authority, the Android Authority newsletter that breaks down the top Android and tech news from the week. The 167th edition is here, bringing this week's newsworthy happening to your inbox.
😱 This week I realized playing a PS5 horror game set in an underground Sumerian temple isn't a great idea if you're (a) afraid of the dark and (b) don't like being underground. Yup, the Dark Pictures Anthology: House of Ashes is every bit as terrifying as it looks!
Google:
- Google acknowledged the display flickering issue with the Pixel 6 Pro — a fix is coming in December.
- And it looks like Pixel 6 phones are accidentally calling random contacts: the bug seems to be related to Google Assistant, but we’re still waiting to hear from Google.
- Google Photo’s Locked Folder feature is coming to iOS next year.
- And Android 12 devices can’t use Chromecast volume controls due to a “legal issue.”
- Also just in: the Pixel 6 charges much slower than implied — that “30W charging” is a myth.
- Meanwhile, Pixel Fold camera details leaked: downgraded performance looks more like the Pixel 5 than the 6.
Samsung:
- There are rumors that we could see the Galaxy S21 FE at CES 2022.
- And a set of photos showing what appears to be a Samsung Galaxy S22 Ultra leaked: it looks remarkably like a Galaxy Note, with an S Pen slot, but the design might not be final.
- Meanwhile, the Galaxy Tab A8 appeared on Geekbench, and we should see it soon, possibly even before Christmas.
- Also this week: We reviewed Samsung’s 25W Wireless Portable Battery — top charging speeds for the latest Galaxy flagships.
Microsoft:
- Microsoft posted its first $20B+ quarterly profit and passed Apple to become the world’s most valuable firm Friday, worth $2.49T.
- And Microsoft’s taking on Facebook in the metaverse race by adding virtual reality avatars and workplaces to Teams.
Apple:
- It might soon be harder to get your hands on a new iPad as Apple trims iPad production to feed chips to iPhone 13.
- Beats Fit Pro launched: Active noise-cancellation and six hours of battery life in a sporty skin.
- Mark Gurman’s Power On newsletter predicted Apple’s AR/VR headset will be a premium device with “advanced chips, displays, sensors, and avatar-based features,” and that we could see it as soon as next year.
- Meanwhile, Apple is no longer the world’s most valuable company — Microsoft posted its first $20B+ quarterly profit, passing Apple, on Friday.
- And crash detection could be coming to the iPhone and Apple Watch in 2022.
- The modified iPhone with USB-C port is up for sale on eBay — and it’s attracting $100,000 bids.
Elsewhere:
- The global chip shortage isn’t over: “some buyers placing new orders are getting delivery dates in 2024.” Elsewhere, BMW pulled touchscreen features from some models.
- DJI unveiled the DJI Mavic 3, the latest in its line of consumer drones, with a Micro Four Thirds camera sensor, 5.1K video, a secondary camera with 28X zoom, and 46 minutes of flight time.
- Facebook’s shutting down its facial recognition system and will delete over a billion faceprints.
- Royole could add a pop-up selfie camera to its next phone, likely the FlexPai 3.
- And the Asus ROG Phone 5S and ROG Phone 5S Pro officially launched in Europe with the Snapdragon 888 Plus, starting at €999 (~$1,158).
- Meanwhile, Nothing has five new products in the works, but no clue as to what they could be yet.
- Finally, head outside on Sunday evening for an unmissable meeting of the moon and Venus: Nasa says it’s going to be “really pretty.”
Movies/TV:
- In case you missed it, Steve Buscemi dressed up as his own meme for Halloween.
- The box office had its best month of 2021 in October thanks to Venom 2 and the new James Bond flick.
- Marvel’s Eternals hit theaters on Friday with a $9.5 million opening night, surpassing Shang-Chi.
- And Chris Pratt, the voice of Mario, will also be voicing Garfield.
- Meanwhile, Finch premiered on Apple TV: Reviews are in but it would probably make a better Pixar short than a two-hour movie.
- Halloween may be over, but Cronos on HBO Max is a treat for Guillermo del Toro fans this November.
- Finally, you can watch Halle Berry go to space in the trailer for Moonfall, landing in theaters on February 4, 2022.
Gaming:
- Netflix games launched globally for Android app users: Just five games are available right now, and you’ll need an active Netflix subscription.
- Call of Duty: Vanguard also launched on Friday, but doesn’t include the main quest for its popular cooperative multiplayer “zombies” mode: it’ll arrive in a few weeks.
- And Overwatch 2 and Diablo IV are delayed again, with no release date in sight, likely 2023.
- Meanwhile, Nintendo released its last free major content update for Animal Crossing: New Horizons earlier than expected on Thursday.
- Sega’s exploring an alliance with Microsoft where it may develop big-budget titles using the Xbox maker’s cloud gaming tech.
- It’s the end of Fornite in China: “Fortress Night” servers are shutting down on November 15 and new players can no longer register.
- Check out the trailer for Bloodborne “demake” Bloodborne PSX, a retro version of the original game, out January 31, 2022.
- And Monday was the 10-year anniversary of Uncharted 3: Drake’s Deception — the NaughtyDog team’s blog post recalls some of their favorite memories.

- Anker PowerCore III Wireless review: Everything in moderation — “It’s neither the largest, nor the fastest, yet it can juice three devices at a time with proprietary PowerIQ technology.”
- Apple iPhone 13 Pro review second opinion: “If you’ve been eyeing an iPhone, the iPhone 13 Pro is as good as it gets.”
- LG Premier Pro Plus review: Feels great, looks great, but lack of software support makes Samsung or Motorola a safer bet.
- Nothing Ear 1 review: Was the hype all for nothing? — Light, comfortable, with decent noise-cancelling and an excellent mic, but minimal ANC and EQ customization.
- Samsung Galaxy Buds 2 review: A more affordable Buds Pro? — “Sound quality is very good and bound to please most ears, and the noise-cancelling edges out that of the Galaxy Buds Pro.”
Features
- With Android 12L, Google must lead by example: “If Google wants to make Android 12L a success, it needs to learn from its history and its mistakes” (Android Authority).
- Tested: The Pixel 6 charges much slower than Google implied — Sadly, that 30W charging is a myth (Android Authority).
- Spiders are much smarter than you think: Apparently, they play mind games, make plans, and even count… eek! (Ars Technica).
- How to Govern the Metaverse: Games are the answer (Wired).
- Human Computer: The Forgotten Women’s Profession — Computer science as we know it might look a lot different without these women (MessyNessyChic.com).
You’re going to want to put your brunch to one side for this, as today we’re talking about worms… Actually, not the creepy, crawly ones — the malicious software ones.
On this week in 1988 — November 2, if we’re being exact, The Morris worm (or internet worm) became one of the first computer worms to be distributed via the internet. It was also the first time a computer worm had gained the attention of the mainstream media to such a degree.
It was the 80s, so computers, and their programming, weren’t yet part of everyday life in the US. There were around 60,000 computers connected to the internet and computers were generally thought of as for academia and government purposes. Those developing and learning about computer technology saw this as their playground.
Who created the Morris worm?
The Morris worm was named after its creator, Robert Tappan Morris, a programming student at Cornell.
- Morris was the son of Robert Morris, Sr., a computer professional and cryptographer who worked for Bell Labs and later the US National Security Agency (NSA). He made significant contributions to UNIX, including the bc programming language, the program crypt, and the el encryption scheme used by passwords. He’s also known as one of CoreWar’s creators, a game thought to be one of the predecessors of computer viruses…
- Nobody really knows Morris’ motives for sure when he created the worm, and there are those who say he made it as a pen test that went wrong.
- Morris did attempt to cover his tracks, though, hacking into the Massachusetts Institute of Technology network to launch the worm.
- It’s said that a friend of his tipped off the New York Times with Morris’ initials.
- In 1989, he became the first person ever indicted under the US Computer Fraud and Abuse Act, sentenced to a fine of $10,050, three years of probation, and 400 hours of community service.
It’s not all doom and gloom for Morris, though. He went on to become a renowned academic, tech founder, and venture capitalist. He is currently a tenured professor of computer science and artificial intelligence at MIT’s Electrical Engineering & Computer Science department, though we hope these days he’s teaching students how to defend against malware rather than implement it.
What did it do?
The Morris worm actually played a significant role in the history of computer science. This was the first time the “vulnerability” (as we now term it) of networked computers had been demonstrated, leaving developers, students, scientists, and government officials, fearing what would come next.
- The worm exploited vulnerabilities in UNIX sendmail, finger, and rsh/rexec. It guessed weak passwords and used names of account holders to brute force password possibilities.
- Combined with reinfection and compounded repetition, the worm occupied a machine’s resources until they were ultimately shut down. It’s a bit like a DoS or DDoS attack today.
- The worm was pretty clever, too. It would verify whether a new machine was already infected, then only re-infecting previously infected machines one in seven times. This not only accelerated spread but also prevented users from mimicking a worm process to feign infection.
- Around 6,000 computers in total were infected, around 10% of those connected to the web, and following many days of internet chatboard discussion — no WhatsApp in those days — it took two days to fully remove the Morris worm from the machines.
- The cost of damage was estimated to be in the range of $100,000 to $10M.
If you’re interested, you can check out the source code of the threat.
Other famous worms
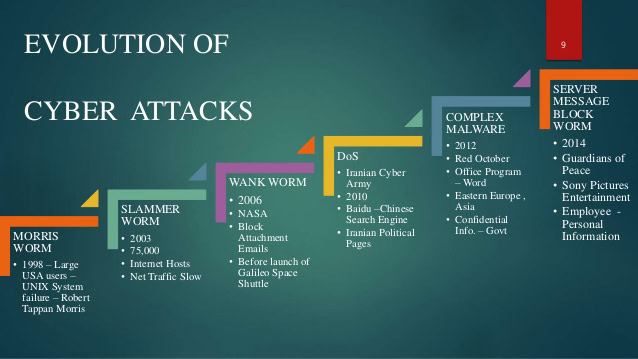
Although an identical Morris worm attack would no longer be viable today as we now take a “security-first” attitude, with password usage and curation more closely monitored, there are plenty of other famous worms that have caused damage and caught our attention throughout history. Here are a few of the most famous:
Jerusalem Virus
Jerusalem, a variant of the Survi virus, actually appeared about a year before the Morris worm, back in 1987. Also known as BlackBox, this malware worked by deleting programs or file executed every year on set days, most notably Friday the 13. It also increased the file size of files running within DOS, depleting resources and slowing down data processing.
ILOVEYOU Worm
The Love Bug Worm, or ILOVEYOU Worm, was created by a college student in the Philippines who intended to steal other users’ passwords. It spread in 2000, accessing Outlook email addresses in a user’s contacts list and overwriting the victim’s files while sending itself across the worldwide web.
Storm Worm
Fake news is everywhere these days, but back in 2007 the Storm Worm, named after the Kyrill storm in Europe, gathered a ton of private data and executed DDoS attacks with a fake email subject line alleging 230 people had died during the Kyrill storm, compelling users to open it. It’s also been seen in emails with subject lines such as “A killer at 11, he’s free at 21 and kill again!”
Sobig Worm
There’s a reason spam folders exist nowadays. Back in 2003, the Sobig Worm made its way through millions of computers by posing as an email with a slightly sinister attachment. The *.pif or *.scr attachment contained malware capable of affecting any host within the vicinity, provided the user downloads and runs the file.
- November 9: Motorola Announcement Holiday Event
- November 9: Poco M4 Pro 5G launch
- November 10: CES Unveiled New York
- November 11: GTA: The Trilogy — The Definitive Edition launches on PS4/5, Xbox Series X/S, Switch
- November 18-19: MediaTek Executive Summit
- November 24-30: Steam Autumn Sale
- November 26-29: Black Friday and Cyber Monday weekend
- November 30-December 1: Snapdragon Tech Summit
Tech Tweet of the Week
Will never get over “The Shining” reimagined as a romantic comedy pic.twitter.com/XJNDZkqcqv— Trung Phan 🇨🇦 (@TrungTPhan) November 2, 2021
And a little something extra: A Muggle used E-Paper to create an actual Daily Prophet replica: It’s amazing stuff.
Have a magical week!
Paula Beaton, Copy Editor



