Affiliate links on Android Authority may earn us a commission. Learn more.
Gary Explains: Is your smartphone spying on you?
Digital privacy is a hot topic. We have moved into an era where almost everyone carries a connected device. Everyone has a camera. Many of our daily activities — from riding the bus to accessing our bank accounts — are done online. The question arises, “who is keeping track of all that data?”
Some of the world’s biggest tech companies are under scrutiny about how they use our data. What does Google know about you? Is Facebook transparent about how it handles your data? Is HUAWEI spying on us?
To try to answer some of these questions, I created a special Wi-Fi network which let me capture every packet of data being sent from a smartphone out to the Internet. I wanted to see if any of my devices were secretly sending data to remote servers without my knowledge. Is my phone spying on me?
Setup
To capture all the data flowing back and forth from my smartphone I needed a private network, one where I am the boss, where I am root, where I am admin. Once I have full control of the network, I can monitor everything that goes in and out of the network. To do this I set up a Raspberry Pi as a Wi-Fi access point. I imaginatively called it PiNet. Next, I connected the smartphone under test to PiNet and disabled mobile data (to be double sure I am getting all the traffic). At this point, the smartphone was connected to the Raspberry Pi but nothing else. The next step is to configure the Pi to forward all traffic it gets out to the Internet. This is why the Pi is such a great device, as many models have both Wi-Fi and Ethernet on board. I connected the Ethernet to my router and now everything that the smartphone sends and receives has to flow through the Raspberry Pi.
There are lots of network analysis tools out there and one of the most popular is WireShark. It enables real-time capture and processing of every data packet flying across a network. With my Pi between my smartphones and the Internet, I used WireShark to capture all the data. Once captured, I could analyze it at my leisure. The advantage of the “capture now, ask questions later” method is I can leave the setup running overnight and see what secrets my smartphone is revealing in the middle of the night!
I tested four devices:
What I saw
The first thing I noticed was our smartphones talk to Google a lot. I guess that shouldn’t surprise me — the entire Android ecosystem is built around Google’s services — but it was interesting to see how when I woke a device from sleep, it scurries off and checks your Gmail and the current network time (via NTP) and a whole bunch of other things. I was also surprised by how many domain names Google owns. I was expecting all the servers to be something.whatever.google.com, but Google has domains with names like 1e100.net (which I guess is a reference to a Googolplex), gstatic.com, crashlytics.com, and so on.
I checked and verified every domain and every IP address the test devices contacted to be sure I knew who my smartphone was talking to.
Besides talking to Google, our smartphones seem quite carefree social butterflies and have a wide circle of friends. These, of course, are directly proportional to how many apps you have installed. If you have WhatsApp and Twitter installed, guess what, your device contacts WhatsApp’s and Twitter’s servers on a regular basis!
Did I see any nefarious connections to servers in China, Russia, or North Korea? No.
Ads
Something your smartphone often does is connect to Content Delivery Networks to get ads. Again, which networks it connects to, and how many, will depend on the apps you install. Most advertising-supported apps will use libraries provided by the ad network, which means the app developer has little or no knowledge of how the ads are actually served or what data gets sent to the ad network. The most common ad providers I saw were Doubleclick and Akamai.
In terms of privacy, these ad libraries can be a controversial topic, because an app developer is basically trusting the platform to do the right thing with the data and only send what is strictly needed to serve the ads. We have all seen how trustworthy ad platforms are during our daily use of the web. Pop-ups, pop-unders, auto-playing videos, inappropriate adverts, ads that take over the whole screen — the list goes on. If ads weren’t so intrusive, there would never be ad blockers.
Amazon AWS
I saw a fair bit of network activity related to Amazon’s Web Services (AWS). As a major cloud server provider, Amazon is often the logical choice for app developers who need databases and other processing abilities on a server, but don’t want to maintain their own physical servers.
Overall, connections to AWS should be considered innocuous. They’re there to provide the services you asked for. However, it highlights the open nature of connected devices. Once you install an app there is potential it can send any and all of the data it has collected to a miscreant, even via a reputable service provider like Amazon. Android guards against this in several ways, including by enforcing permissions on apps, and with services like Play Protect. This is why side-loading apps can be very dangerous.
OK, Google

Since PiNet allowed me to capture every network packet, I was keen to check to see if Google was secretly spying on me by activating the microphone on my Pixel 3 XL and sending the data to Google. When you activate Voice Match on the Pixel 3 XL, it will listen permanently for the keyphrases “OK Google” or “Hey Google.” Listening permanently sounds dangerous to me. As any politician will tell you, an open mic is a hazard to be avoided at all costs!
The device is meant to listen locally for the keyphrase, without connecting to the internet. If the keyphrase isn’t heard, nothing happens. Once the keyphrase is detected, the device will send a snippet to Google’s servers to double-check if it was a false positive. If everything checks out, the device sends audio to Google in real-time until either a command is understood, or the device times out.
That is what I saw.
There is no network traffic at all, even when I talked directly at the phone. The moment I said”Hey Google” a real-time stream of network traffic was sent to Google, until the interaction stopped. I tried tricking the Pixel 3 XL with slight variations of the keyphrase like “Pray Google” or “Hey Goggle.” Once I managed to get it to send a snippet to Google for further validation, but the device didn’t get confirmation and so Assistant didn’t activate.
What does Google know about me?
Google offers a service called Takeout which allows you to download all your data from Google, ostensibly so you can migrate your data to other services. However, it is also a good way to see what data Google has on you. If you try to download everything the resulting archive can be huge (maybe more than 50GB), but that will include all your photos, all your video clips, every file you have saved on Google Drive, everything you uploaded to YouTube, all your emails, and so on. As a way to check privacy, I don’t need to see which photos Google has, I know that already. Likewise, I know what emails I have, what files I have on Google Drive, and so on. However, if I exclude those bulky media items from the download and concentrate on activity and metadata, the download can be quite small.
I downloaded my Takeout recently and had a poke around to see what Google knows about me. The data arrives as one or more .zip files containing folders for each of the different areas including Chrome, Google Pay, Google Play Music, My Activity, Purchases, Task, and so on.
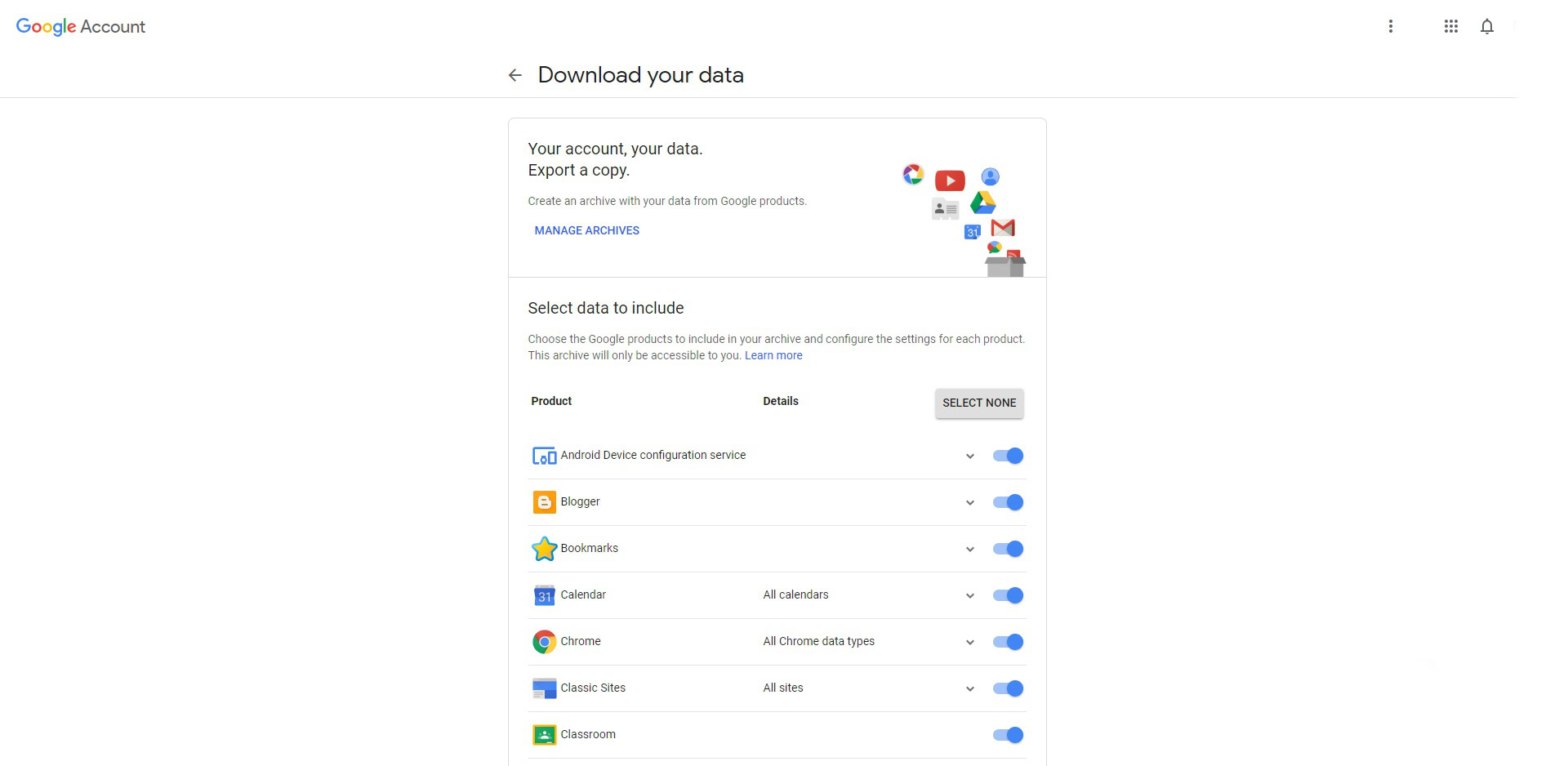
Diving into each folder shows what Google knows about you in that area. For example, there is a copy of my Chrome bookmarks and a copy of the Playlists I created on Google Play Music. At first, there was nothing surprising. I expected a list of my Reminders, since I created them using Google Assistant, so Google should have a copy of them. But there were one or two surprises, even for someone as “tech savvy” as me.
The first was a folder of MP3 recordings of everything I ever said to my Google Home mini. There was also an HTML file with a transcript of all those commands. To clarify, these are commands I gave the Google Assistant after it was activated with “Hey Google.” To be honest I didn’t expect Google to keep an MP3 file of all my commands. OK, I get that there is some engineering value in being able to check the quality of Assistant, but I don’t think Google needs to keep these audio files. It’s a bit much.
There was also a list of all the article I have ever read on Google News, a record of every time I played Solitaire, and all the searches I have made on Google Play Music going back almost five years!
It turns out Google processes all your email messages looking for purchases and creates a record of them.
The one that really shocked me was in the Purchases folder. Here Google had a record of everything I have ever purchased online. The oldest item was from 2010, when I purchased some airplane tickets. The point here is that I didn’t buy these tickets, or any of the items, via Google. I have purchase records for items from Amazon, eBay, and iTunes. There are even records of birthday cards I bought.
Digging deeper I started to find purchases I didn’t make! After some head scratching it turns out that these records are the results of Google processing my email messages and guessing at purchases I have made. You have probably seen this especially with regards to flights. If you open an email from an airline, Gmail helpfully puts some summary information about your flight in a special tab at the top of the message.
It turns out Google processes all your email messages looking for purchases and creates a record of them. When someone forwards you an email about something they have purchased, Google can even inadvertently parse it as a purchase you have made!
What about Facebook, Twitter, and others?
Social media and privacy are in some ways contradictory. As Harold Finch said in the TV show Person of Interest about social media, “The government had been trying to figure it out for years. Turns out most people were happy to volunteer it.” With social media, we willingly post information including birthdays, names, friends, colleagues, photos, interests, wish lists, and aspirations. Then, having published all that information, we are shocked when it is used in ways we didn’t intend. As another famous character said about a gambling hall he frequented, “I’m shocked, shocked to find that gambling is going on in here!”
All the big social media sites, including Facebook and Twitter, have privacy policies and they are fairly broad in what they cover. Here is a snippet from Twitter’s policy:
“In addition to information you share with us, we use your Tweets, content you’ve read, Liked, or Retweeted, and other information to determine what topics you’re interested in, your age, the languages you speak, and other signals to show you more relevant content.”
So, is your device connecting to Twitter and allowing Twitter to determine things like your age, the language you speak, and what things interest you? Sure.
It profiles you — and you let it do that.
Here is the key question: if I didn't have a smartphone, would that stop entities from spying on me if they wanted to?
Potential vs Actual
The biggest problem with connected devices and online entities is not what they are doing, but what they could do. I used the phrase “entities” intentionally because the dangers around mass surveillance, spying and profiling are not just about Google or Facebook. Ignoring genuine software mistakes (bugs) as well as the standard business models of big online companies, it is fairly safe to say Google isn’t spying on you. Neither is Facebook. Neither is the government. That doesn’t mean they can’t — or won’t.
Is some hacker or government spy somewhere activating the mic on your phone to listen to you? No, but they could. As we saw recently with the events surrounding the murder of Jamal Khashoggi, entities can trick you into installing an app that spies on you. Companies like Zerodium sell zero-day vulnerabilities to governments, which could allow malicious apps (like Pegasus) to be installed on your device without you knowing.
Did I see any such activity with my devices? No, but I’m not a likely target for such surveillance and skullduggery. It could still happen to someone else.
Here is the key question: if I didn’t have a smartphone, would that stop entities from spying on me if they wanted to?
Before the launch of smartphones, every major government in the world was already involved in spying and surveillance. World War II was probably won by breaking of Enigma code and gaining access to the intelligence it hid. Smartphones aren’t to blame, but now there is a larger attack surface — in other words, there are more ways to spy on you.
Wrap-up
Following my testing, I am confident none of the devices I used are doing anything unusual or malevolent. However, the issue of privacy is larger than just a device which isn’t being intentionally malicious. The business practices of companies like Google, Facebook, and Twitter are highly debatable and they often seem to push the boundaries of privacy.
As for spying, there’s no white van parked outside my house watching my movements and pointing a directional microphone at my windows. I just checked. Nobody’s hacking my phone. That doesn’t mean they can’t.