Affiliate links on Android Authority may earn us a commission. Learn more.
Android P security: snooping forbidden

As well as a whole raft of new features, Android P includes some substantial security improvements including blocking apps from recording you secretly and more encryption for backups. Android P’s security improvements aren’t just about fixing bugs and closing loopholes — that’s more what Google’s monthly security updates are for. These changes modify the design of the OS and alter its policies to enhance security.
Probably the biggest change is the new restrictions about what apps can do in the background. Android P limits an app’s access to the mic, camera, and sensors when an app goes idle. This means when an app is idle, the mic will report empty audio and sensors will stop reporting events. Cameras used by an app are disconnected and Android P will generate an error if the app tries to use them.

The upshot of this is that an app needs to be running in the foreground or running as a foreground service (with an icon in the notification area) for it to be able to record audio. For most apps this isn’t a problem as their use of the mic or the camera is intentional and well advertised — malicious apps, some of which record you in the background when you switch away to do another task, are what will struggle with this.
Encrypted backups
The use of the cloud has become the norm. We rarely think about the implications of using someone else’s servers to hold our private and confidential data. While all data backed up from your Android device to Google’s servers is encrypted, it is encrypted by Google for Google. In other words Google can still access it. There are a whole bunch of ethical and legal issues around the encryption of user data, but one major big change in Android P is that now backups are encrypted with a client-side secret. This means your PIN, pattern, or password is used to encrypt your data before it leaves your device.
The changes in Android P are about modifying the design of the OS or altering its policies so that security is enhanced.
As before, your data travels over a secure, encrypted connection to Google’s servers, only now the actual data is encrypted using a password that only you know! This also means your PIN, pattern, or password is required to restore data from the backups. If you forget your PIN then your data is lost, but that is probably a risk worth taking. Google is ensuring the validity of these encrypted backups using its custom security chip, Titan.
For the first developer preview this feature is “still in active development.” It will be fully launched in a future Android P preview release.
Targeting modern Android
Android has often been attacked for its so-called fragmentation problem. Without getting into all the whys and hows of fragmentation, one aspect harms the ecosystem overall — the slow migration to new APIs and services. Though each version of Android brings new functionality, many app developers target the lowest common denominator, ignoring enhancements for devices running newer versions of Android.
This has security implications, especially when it comes to big changes like the introduction of runtime permissions with Android 6.0. At the end of 2017, Google announced some changes to the Play Store. By November 2018, Google will require all apps (and app updates) to target at least Android Oreo (the “targetSDKVersion” needs to be 26 or higher). In 2019 apps will also need to include 64-bit native libraries along with 32-bit versions. That doesn’t mean Android’s support for 32-bit is going away — apps with a 32-bit library will just need to have a 64-bit version too.
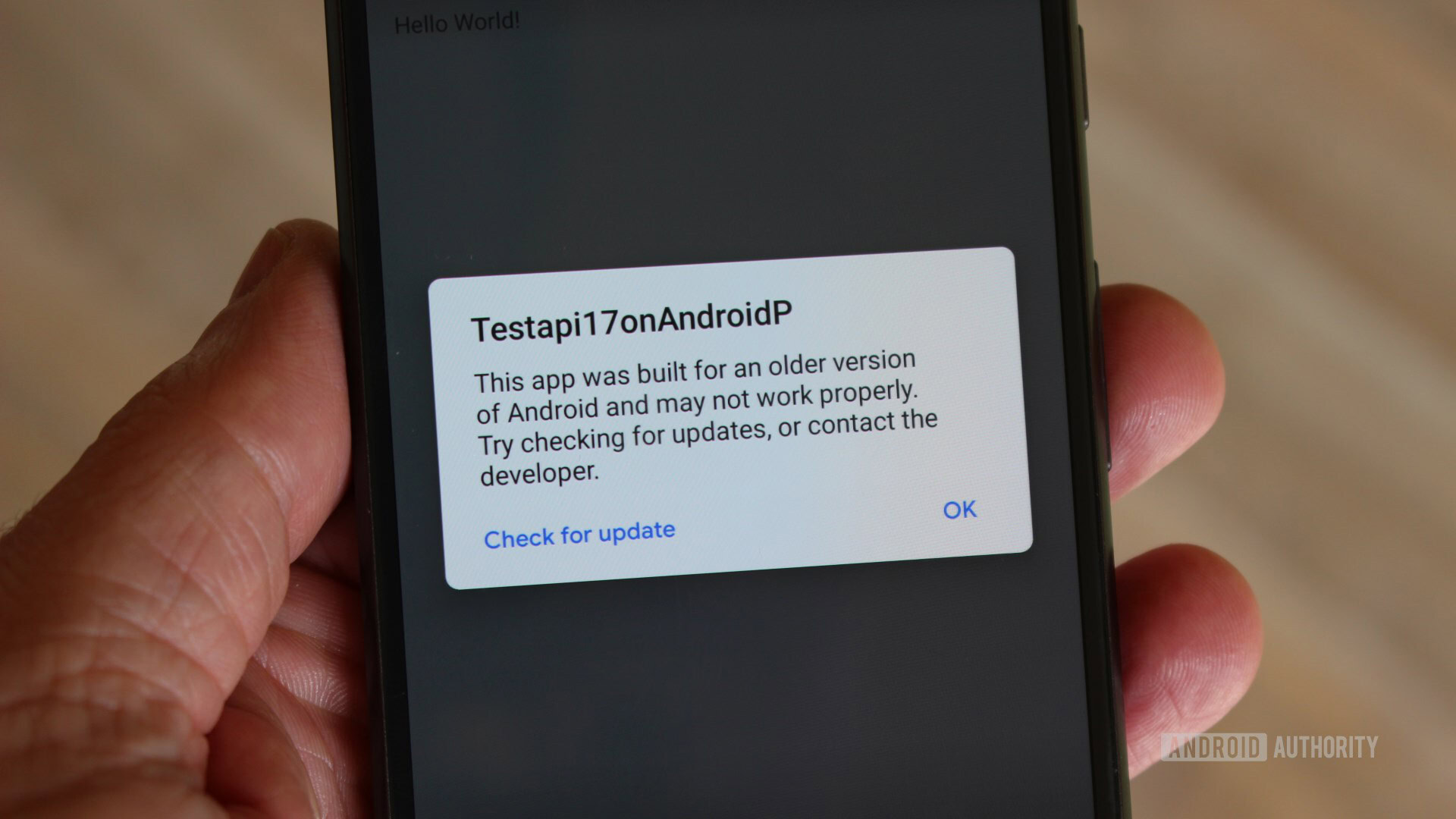
At a platform level, Android P will warn users when they install an app targeting a platform earlier than Android 4.2 (API 17). Google says that future Android versions will continue to increment this lower bound. This ensures apps are built with the latest APIs and therefore the latest security enhancements.
Cleartext forbidden
Android’s Network Security Configuration feature includes functionality to check if an app is making unsecured HTTP connections (rather than secure HTTPS) connections. Apps designed to only make encrypted connections can enabled the “Cleartext traffic opt-out” setting and prevent accidental regressions in apps due to changes in URLs, which might have mistakenly dropped the “S” in HTTPS. When cleartext network traffic is not permitted, Android’s components (HTTP and FTP stacks, among others) will refuse make unencrypted connections.

Wrap-up
These security related changes are a welcome addition to Android P and should help promote a safer and more secure experience for all users. They also ensure app developers will follow the latest guidelines and requirements from Google.
What do you think? are these worthwhile changes? Is switching off the mic feature for idle apps good? Let me know in the comments below!