Affiliate links on Android Authority may earn us a commission. Learn more.
This is how Google finds Android malware

Google has outlined its process for finding malware via the Android Developers blog. In the post, Google Software Engineer Megan Ruthven discusses Android’s Verify Apps safety protocol — used to determine potentially harmful apps installed on a device — and what happens when a device stop communicating with it.
Verify Apps is a security function that routinely scans apps downloaded from the Play Store to ensure that they are safe but Ms Ruthven notes that sometimes phones cease interacting with it, perhaps through something as innocuous as buying a new handset.
When a device stops communicating with Verify Apps, it is considered Dead or Insecure (DOI). An app which has a “high enough percentage of DOI devices downloading it,” is then said to be a DOI app. Conversely, if a device continues to check in with Verify Apps following an app download, it becomes known as “retained.”

Android gives apps a DOI score based on the number of number of devices that downloaded the app, the number of retained devices that downloaded the app and the probability of a device downloading any app that will be retained, to determine whether or not an app could pose a threat. Here’s the formula for how the Android security team calculates this:
N = Number of devices that downloaded the app.
x = Number of retained devices that downloaded the app.
p = Probability of a device downloading any app will be retained.
Z = DOI score
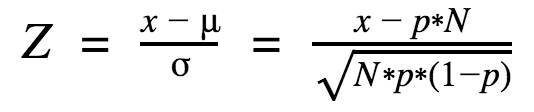
If the DOI score falls below “-3.7,” it indicates that a significant number of phones and/or tablets stopped checking with Verify Apps after installing the app in question. Google then combines the score with “other information” to ascertain whether it is indeed harmful, before taking action such as removing existing or preventing future installs.
Ms Ruthven notes that the implementation of this security process has contributed to the discovery of apps containing malware such as Hummingbad, Ghost Push, and Gooligan.