Affiliate links on Android Authority may earn us a commission. Learn more.
How to secure your Android phone and protect your data
A recent report by Check Point, the firewall maker, estimated that €36+ million has been stolen from corporate and private bank accounts in Europe by a group running a campaign of attacks known as “Eurograbber”. The campaign infected victim’s mobile phones with a piece of malware which could intercept SMS messages. When the victim used their online banking the SMS authentication code sent to the phone was intercepted. This then allowed the attackers to access the victim’s account.
Securing your smartphone and protecting yourself against malware isn’t about stopping some annoying virus getting on your device, it is about protecting your money, data and privacy.
There are several different areas in which you can improve your phone’s security including physical access, malware protection and encryption.
Who has access to your phone?
RULE #1 – Never leave your phone laying around where uninvited guests can access it
Before looking at things like malware and data stealing apps, the simplest form of security is to limit physical access to your phone. There maybe lots of sophisticated remote attacks out there but if all I need to do is quickly pickup your phone and access your emails, PayPal, eBay or Amazon account while you pop off to get a coffee then all the security software in the world won’t do you any good.
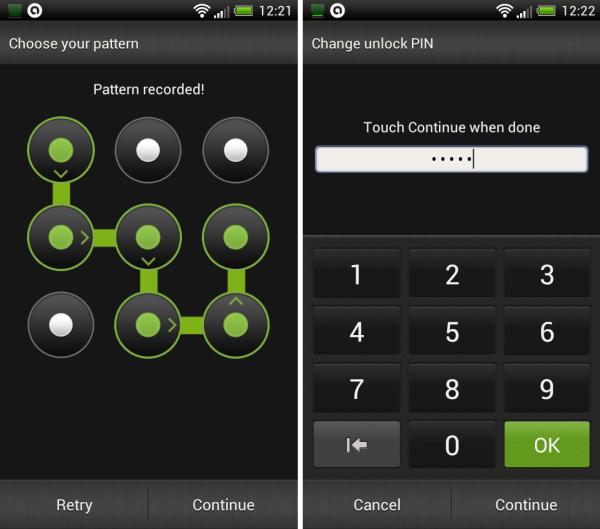
It is also essential that you use a lock screen. This stops everyone from small kids to determined snoopers from sneakily accessing your device. Modern Android versions have a whole gamut of lock screen options including pattern unlock, PIN numbers and password protection. To set these go to Settings and then tap Security. You can also customize how quickly the lock is automatically applied.
RULE #3 – Set a PIN to protect purchases on Google Play
It is also possible to set a PIN for purchases in Google Play. With the PIN any would-be trickster (or small child) won’t be able to buy content from Google’s app store. To set it, start the Google Play app, go to setting and then tap “Set or change PIN”. After the PIN is set, tap “Use PIN for purchases” to require the PIN before purchasing anything from the store.
RULE #4 – Install a phone location app or use a security app with an anti-theft component
Keeping your phone nearby and using a lock screen will thwart snoopers but the determined criminal will simply just walk away with your phone and try to extract the data later or simple wipe your phone and try and selling it. The first few hours after you phone has been taken are the most critical. To find your phone it is important to use a phone location service like Where’s My Droid or install a security app with an anti-theft option like avast! Mobile Security.

RULE #5 – Don’t install apps from dodgy third party sites, stick to places like Google Play or the Amazon appstore
Because Android is so popular, it is normal for it to become a malware target. Malware authors don’t waste their time writing malware for a phone operating system that no one is using. This means that there is lots of Android malware out there. But here is thing, how does Android malware spread? Unlike worms, which spread automatically over the network or viruses which tend to spread via USB flash drives etc., the majority of Android malware needs to be installed manually. There have been some exceptions but in general it is unsuspecting users that install the malware themselves onto their own phones.
The malware authors have lots of dirty tricks to try and fool potential victims into installing their malware. One very common approach is to offer a free version of a popular non-free app with the malware hidden inside the app. Greedy users who think they are getting a bargain because they have managed to save $0.69, but in fact are infecting their devices with malware. Over 99% of Android malware is spread via third party app sites. Don’t use them.
RULE #6 – Always read the reviews of apps before installing them
RULE #7 – Check the permissions the app needs. Games generally don’t need to send SMS messages etc
A small percentage of malware is spread via Google Play, but the apps in question normally only survive a few hours on the store before being removed. To avoid such rare cases it is always important to read the reviews of other users and always check the app permissions.
RULE #8 – Never follow links in unsolicited emails or text messages to install an app
If the malware authors can’t get you via a third party store or their apps are taken down from Google Play, they have one more trick, unsolicited emails and text messages asking you to install an app. In the “Eurograbber” campaign, what the attackers did was infect the victim’s PC with a piece a malware (something which is a lot easier than infecting an Android phone) and then via that malware they tricked the user into installing their “enhanced security” app on their phone. The PC malware monitored the victim’s Internet usage and when they went to an online banking site the malware pretended to be a warning from the bank telling them to install an app on their smartphone. It was all downhill from there for the poor victim.
RULE #9 – Use an anti-virus / anti-malware app
Even with diligence it is possible for malware to find its way on to your device. It is therefore important that you install an anti-virus / anti-malware app. This best antivirus apps for Android article will help you choose one, but if you don’t have time right now then go for Kaspersky Mobile Security (paid) or avast! Mobile Security (free).

RULE #10 – Don’t root your phone unless you absolutely need to
Some of my colleagues here at Android Authority are very keen on rooting and I can understand why. The lure of custom ROMs and the ability to tweak different parts of the OS are all part of what makes Android great. But, Android was designed with a very particular security model which limits what an app can do. By rooting a device this security model breaks. Even the CyanogenMod team acknowledged that there are limited uses for root and none that warrant shipping the OS defaulted to unsecured. The problem is there are specific types of Android malware that circumvent Android’s security mechanisms by using the existing root access. With root access, the malware can access parts of Android that are supposed to be protected by the permissions system.
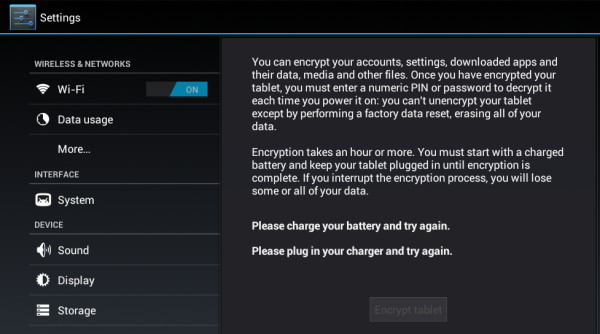
RULE #11 – If your device has valuable data on it then use encryption
Since Android 3 it is possible to use full encryption on a phone or tablet. By encrypting your device all the data including your Google Accounts, application data, media and downloaded information etc. becomes inaccessible without the right password or PIN. Every time you boot the device you must enter the PIN or password to decrypt it. If your device has valuable data on it using this encryption is a must. NASA recently had an embarrassing episode where a laptop was taken that held personally identifiable information of “at least” 10,000 NASA employees and contractors. After the incident NASA decided that any devices that leave a NASA building need to use full disk encryption.
RULE #12 – Use a VPN on unsecured Wi-Fi connections
While on the subject of encryption it is worth remembering that if you are using a public unsecured Wi-Fi hot spot all of the data that is send using http:// (rather than https://) can be seen my any network snooper. In the past security researchers have shown how easy can be to steal passwords to the popular social networking sites just by using a laptop and waiting around near a public open hot spot. To avoid revealing your password and other data, don’t use open Wi-Fi hot spots or use a virtual private network (VPN) to secure your connection.
Conclusion
If you follow these twelve rules and remain vigilant you should never have any security troubles with malware, thieves, hackers or any small furry animals! OK, that last part isn’t true, but the rest is!