Affiliate links on Android Authority may earn us a commission. Learn more.
Google attempts to tackle Stagefright with Android N changes
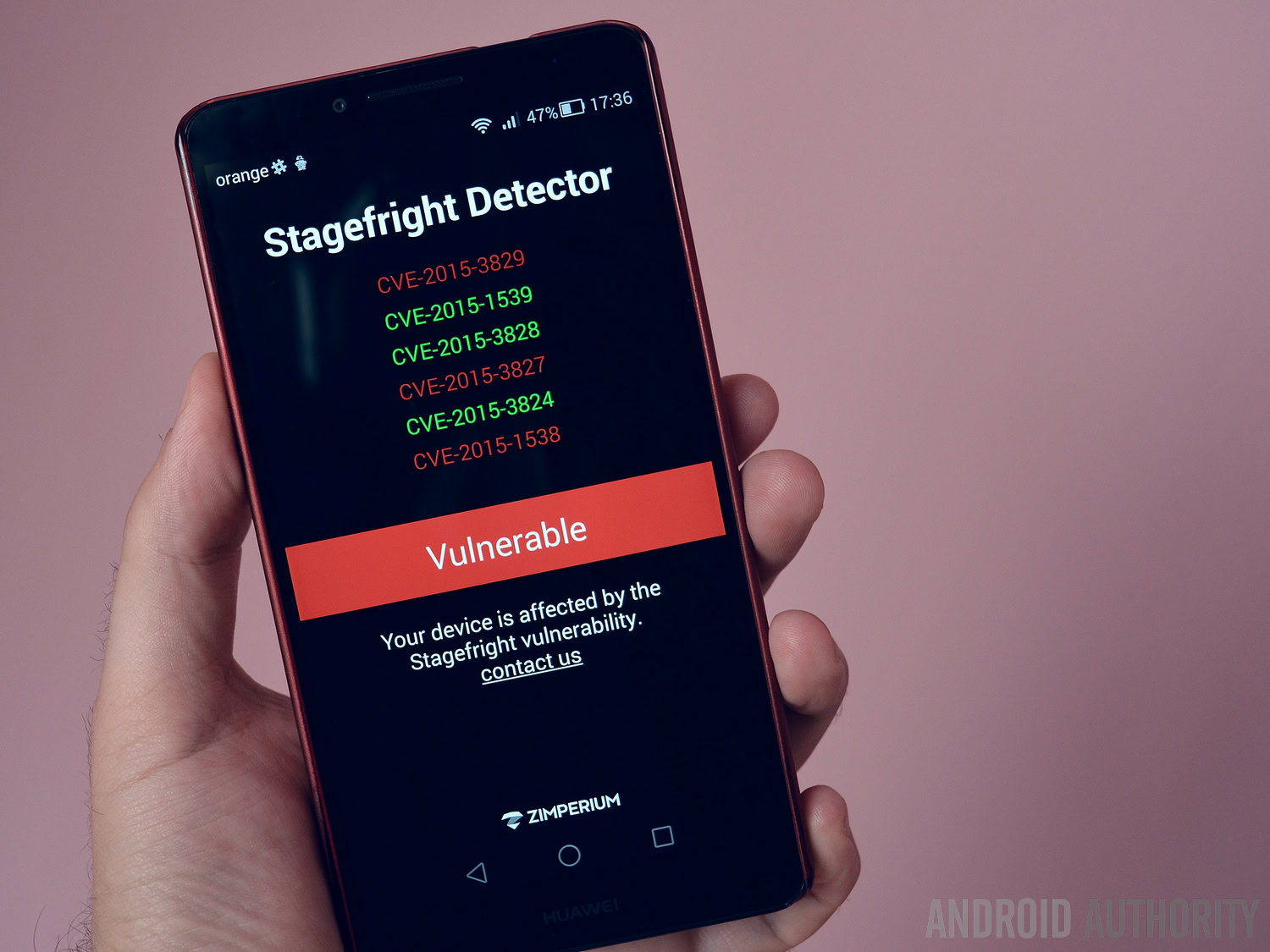
The Stagefright scare last year was one of the most well-publicized Android vulnerability stories ever. It allowed hackers to remotely execute malicious code and escalate permissions to essentially take over all parts of the Android system controlled by the mediaserver (including the camera, microphone, Bluetooth, Wi-Fi, graphics and more). With the intention of stamping out repeat Stagefright scenarios in future, Google is introducing core changes to the way mediaserver permissions function in Android N.

In a post on the Google Developer’s Blog called ‘Hardening the media stack’, Google outlines the ways it has mitigated the possibility of future vulnerabilities using the libstagefright library. Long story short, Google has divided up the various processes controlled by the mediaserver and sandboxed their permissions. So in Android N, “the cameraserver may access the camera, only the audioserver may access Bluetooth, and only the drmserver may access DRM resources.”

This kind of separation means that any future vulnerabilities would be confined to a much smaller part of the system rather than the whole mediaserver gamut. As Google notes, “Gaining code execution in libstagefright previously granted access to all the permissions and resources available to the monolithic mediaserver process including graphics driver, camera driver, or sockets, which present a rich kernel attack surface. In Android N, libstagefright runs within the mediacodec sandbox with access to very few permissions.”
Any future vulnerabilities would be confined to a much smaller part of the Android system.
Google has also changed the way Android N handles both signed and unsigned integer overflows (which comprised the majority of Stagefright vulnerabilities). “In Android N, signed and unsigned integer overflow detection is enabled on the entire media stack, including libstagefright. This makes it harder to exploit integer overflows, and also helps to prevent future additions to Android from introducing new integer overflow bugs.”
Google assures us that hardening the media stack is an ongoing process and welcomes feedback from developers, researchers and white hat hackers on its goal to improve the sandboxing in Android N. These efforts are not just restricted to the mediaserver either, with Google promising that “these hardening techniques—and others—are being actively applied to additional components within Android.”
What are your thoughts on Android security? Are you happy with Google’s response to Stagefright?