Affiliate links on Android Authority may earn us a commission. Learn more.
Google shatters SHA-1, but don't worry: the Internet is still working

Whole areas of modern computing rely on the concept of certain things being “computationally infeasible” including encryption. “Computationally infeasible” means mean that certain mathematical operations are logically possible, however to actually perform them you need lots of time (like years) and lots of computing power.
But sometimes shortcuts can be found which speed up these calculations. In the field of encryption, these shortcuts are known as weaknesses, as they reduce the amount of time need to perform the calculations and therefore make them more computationally feasible – not infeasible.
The news today is that Google has found more new weakness in the SHA-1 hashing algorithm which means that it can create fake hashes.
The SHA-1 hashing algorithm is a way of producing a unique identifier for any given block of data, typically a file or an encryption certificate. That SHA-1 hash is a bunch of numbers, like this:
44e63796bb58db4a79268f625c95e1c212837602So if I download a file from the Internet I can check that the download is good by comparing the SHA-1 hash of the file I have downloaded with the hash published on the website. If they match then I know that the file I have and the published file are the same. If the file was different, even by one single character then the SHA-1 hash would be different and I would know that something has gone wrong.
The same principle applies to encryption. We all use https:// secure sites every day, not only for online banking or for online shopping, but also for searches on Google or for accessing our email. It stops third parties from snooping at our search requests or from stealing credit card details.

When you connect to a https:// site the web browser needs to know that it really has connected to the right site and not a fake site set up by cybercriminals. The TLS protocol used for https:// checks a site’s authenticity by asking for its certificate. The browser then checks the certificate to see if it is genuine. That check uses hashes like SHA-1.
Essentially what happens is that the certificate is digitally signed by a third party, known as a Certificate Authority (CA) and to ensure that the certificate is the same as the one verified by the CA then a hash is used. In other words, if you see a certificate with this hash then it is good.
So, if you can create a fake certificate that has the same hash as a good certificate then web browsers all over the world will be tricked into accepting the fake certificate.

Up until a few years ago the hash algorithm used to confirm the digital signature was SHA-1, but since 2016 all the certificate authorities stopped issuing SHA1-based certificates and the major web browsers started to warn users when accessing secure sites that use SHA-1.
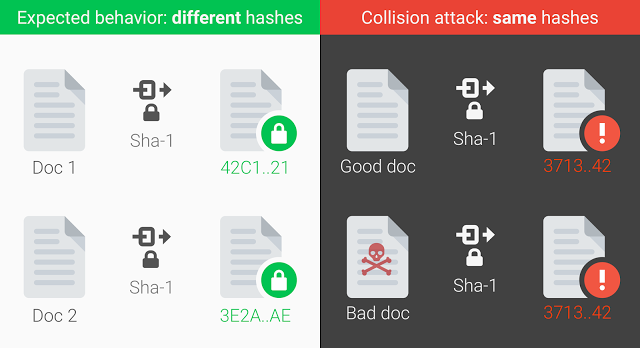
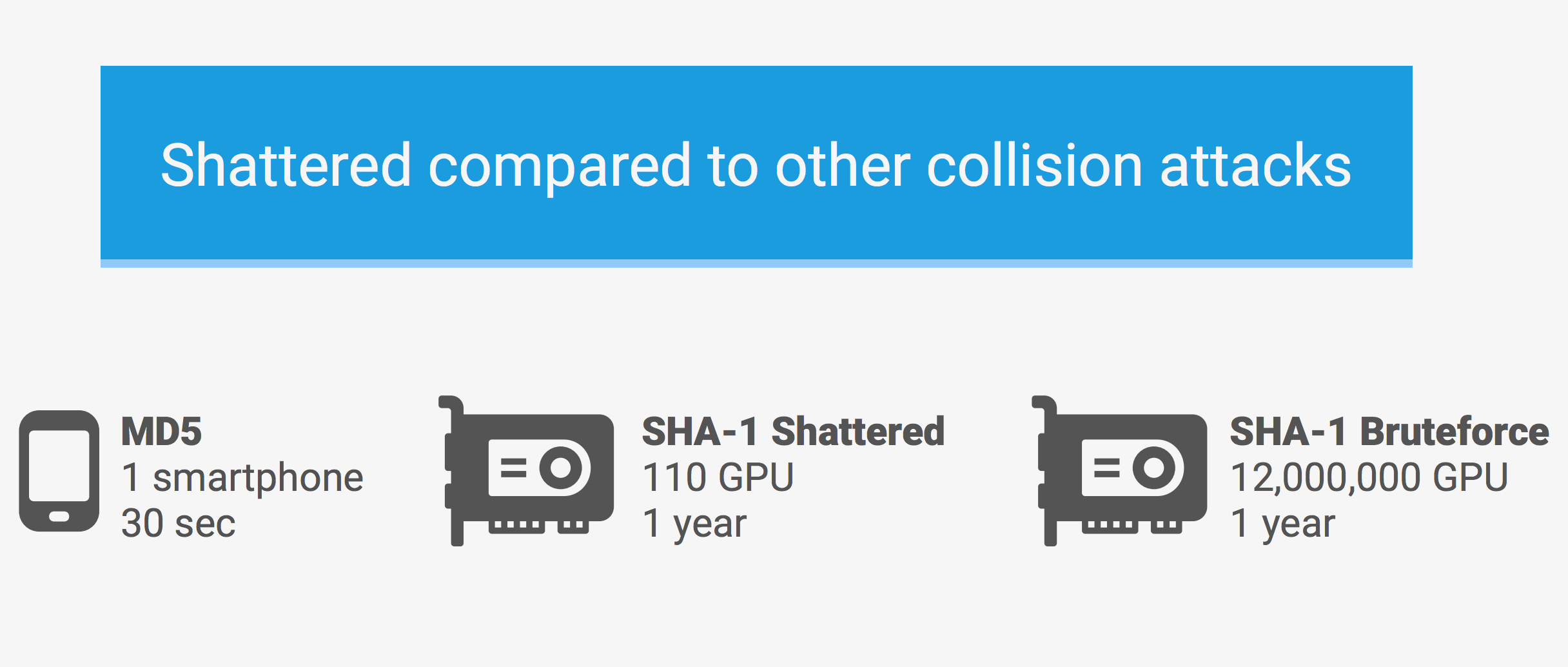
What Google has managed to do is create two PDF files with exactly the same SHA-1 hash. This could theoretically be extended to website certificates. There is however a minor catch, although Google managed to create these two hashes, it took the equivalent of 6500 CPU years and 100 GPU years to do it. So while you or I won’t be making fake SHA-1 hashes any time soon, this amount of computing power isn’t beyond the reach of nation states.
Google has released a comprehensive research paper (PDF) about its work, however it has decided to wait 90 days before releasing the source code.
In order to prevent this attack from active use, Google has added protections into Gmail and GSuite that detects its new collision technique. It has also launched a free detection system to the public.
It isn’t only the web security that is affected but any other systems that use SHA-1 like Git and some backup solutions. Google’s recommendation is that everyone using SHA-1 migrates to safer cryptographic hashes such as SHA-256 and SHA-3.