Affiliate links on Android Authority may earn us a commission. Learn more.
Samsung flagship phones were vulnerable to a stealthy data-stealing attack for a year

- A sophisticated Android spyware called “LANDFALL” targeted Samsung Galaxy devices via a zero-day vulnerability in the company’s image parsing library.
- LANDFALL was deployed through malicious DNG images sent via messaging apps. It enabled attackers to steal sensitive user data without user interaction and while evading detection.
- The issue affected several high-profile Galaxy models in 2024 and was patched by Samsung in April 2025.
Samsung Galaxy phones are among the best Android phones available, particularly if you prioritize robust security, as they offer extended software update support and regular security patches. However, even the best can fall victim to malware at times, and a new report suggests that Samsung Galaxy phones were targeted with the “LANDFALL” spyware. This sophisticated zero-day attack could steal personal data and has reportedly been used in the wild.
Don’t want to miss the best from Android Authority?
- Set us as a favorite source in Google Discover to never miss our latest exclusive reports, expert analysis, and much more.
- You can also set us as a preferred source in Google Search by clicking the button below.
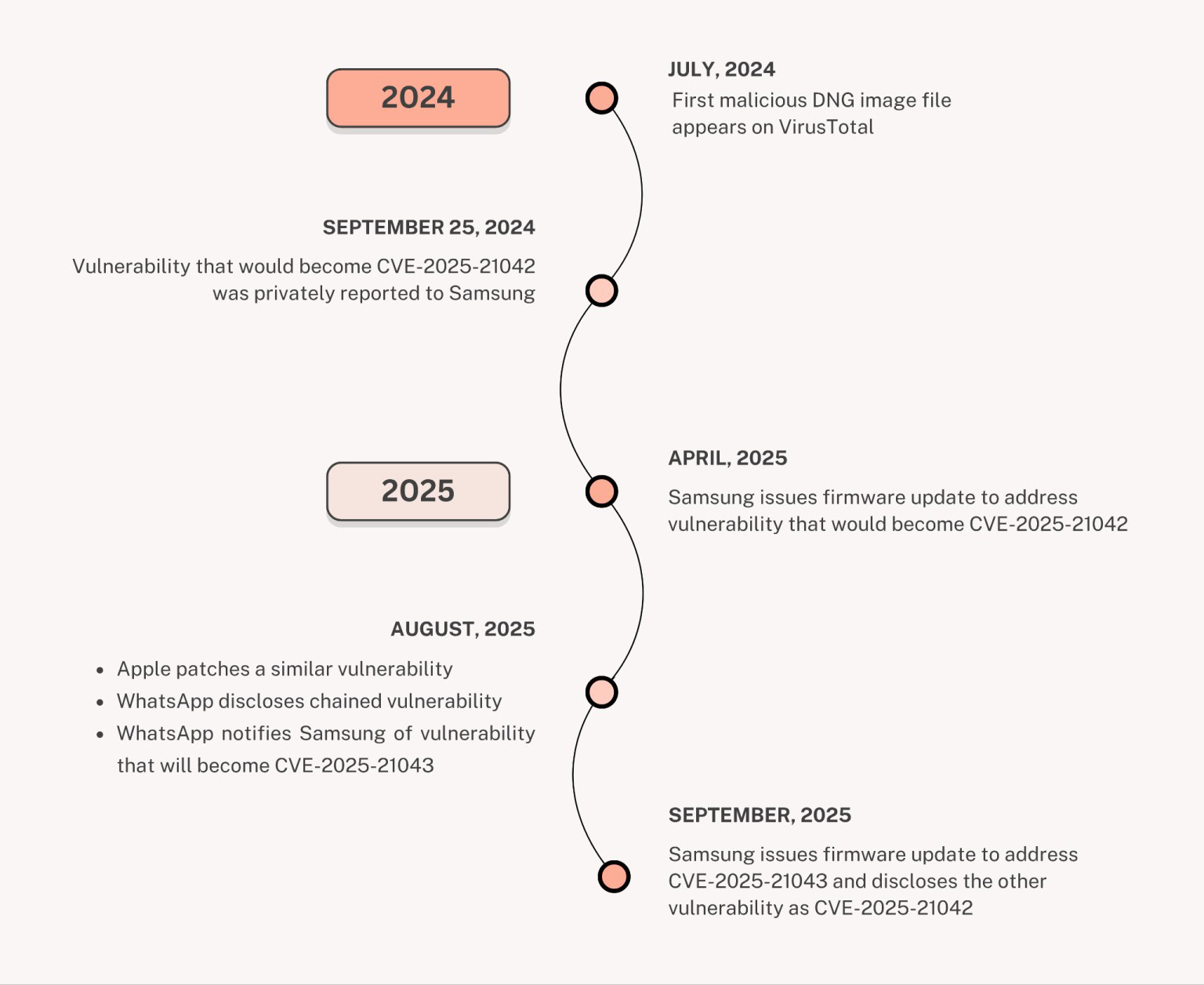
Global cybersecurity company Palo Alto Networks’ Unit 42 division has uncovered a previously unknown Android spyware family that they have named “LANDFALL” (h/t ArsTechnica). This spyware is part of a broader pattern of similar issues that have been found and patched on multiple mobile platforms, including iOS.
On Android and specifically Samsung Galaxy phones, attackers exploited a zero-day vulnerability in Samsung’s Android image processing library to deliver spyware for surveilling individuals. The vulnerability is said to have been actively exploited in the wild before Samsung patched it in April 2025, but that is months after reports of in-the-wild attacks.
What makes LANDFALL particularly devious is that it is a zero-day vulnerability — it could compromise the phone without the user’s direct involvement. With LANDFALL, attackers used a malformed DNG file that was embedded with spyware and distributed through messaging apps, such as WhatsApp.
When the phone processed this malformed image, it inadvertently loaded the spyware along with it. The spyware then enabled remote operators to extract data, including photos, contacts, call logs, microphone recordings, and location tracking data. The spyware also included tools that helped it evade detection and become difficult to remove, allowing it to remain active and undetected for months.
Unit 42 believes LANDFALL was active in 2024 and early 2025 in regions in the Middle East and was used in targeted intrusion activities. Samsung’s One UI 5 through One UI 7 versions (i.e., based on Android 13 through 15) are potentially vulnerable, and targeted device models are said to include the Galaxy S22, Galaxy S23 series, Galaxy S24 series, Galaxy Z Fold 4, and Galaxy Z Flip 4.
While there’s no ongoing risk to current-generation Samsung users, as Samsung has already patched the vulnerability, it’s best to ensure that your Samsung Galaxy phone is updated to the latest Android version and security patch available. While this particular spyware has not been reported to be used in Western regions, it’s better to be safe than sorry.
We’ve reached out to Samsung for comments and will update this article as soon as we receive more information.
Thank you for being part of our community. Read our Comment Policy before posting.