Affiliate links on Android Authority may earn us a commission. Learn more.
What is Pegasus and how is it used for spying?
Government sanctioned cyber-surveillance came back into the news in 2021, following an exposé by The Guardian and 16 other media organizations that revealed how commercial malware is being used by authoritarian regimes used to target activists, politicians, and journalists. But it didn’t stop there. In May 2022, it was revealed that the very same spyware was being used to target Catalan independence leaders and Spanish politicians – including the prime minister. The commercial malware in question is called Pegasus and it is sold, for millions of dollars, by an Israeli company called NSO Group.
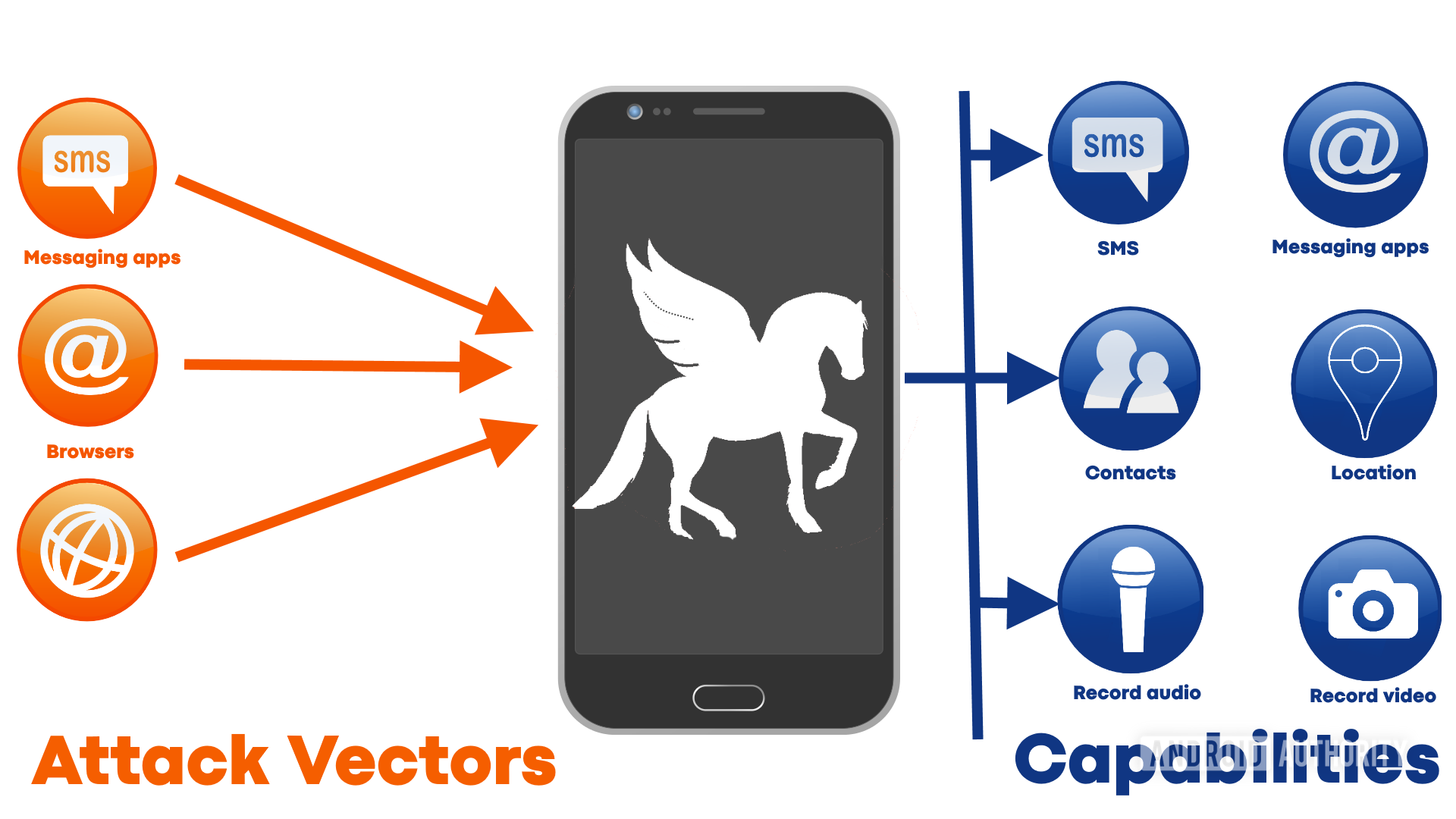
Pegasus, which is the most sophisticated piece of spyware we know about, has the potential to record calls, copy messages, and secretly film the owner (and those nearby) on any device that has been compromised.
What is Pegasus Spyware?
In short, Pegasus is commercial spyware. Unlike the malware used by cybercriminals to make money by stealing from and cheating their victims, Pegasus is designed solely for spying. Once it has secretly infected a smartphone (Android or iOS), it can turn the device into a fully-fledged surveillance device. SMS messages, emails, WhatsApp messages, iMessages, and more, are all open for reading and copying. It can record incoming and outgoing calls, as well as steal all the photos on the device. Plus it can activate the microphone and/or the camera and record what is being said. When you combine that with the potential to access past and present location data, it is clear that those listening at the other end know almost everything there is to know about anyone that is targeted.
You need to know that if a government agency is targeting you with software like Pegasus, and you insist on keeping your smartphone, then there is little you can do to stop it.
The earliest versions of Pegasus were spotted in the wild as far back as 2016, so this isn’t something new. However, its capabilities and its sophistication have grown enormously since those early days. Not just anyone can get hold of a copy of Pegasus — this isn’t something sold on eBay or even on the dark web. NSO Group only sells it to governments and it costs millions to buy.
Thankfully, this means it isn’t in the hands of rogue bands of cybercriminals or terrorists. In fact, NSO Group markets Pegasus as a “technology that helps government agencies prevent and investigate terrorism and crime to save thousands of lives around the globe.” Sounds noble. Except of course that being a “government” is no assurance of character, morals, or self-restraint. Some of the governments that are using the Pegasus spyware to target journalists, business executives, religious leaders, academics, and union officials include Hungary, Mexico, Saudi Arabia, India, and the United Arab Emirates (UAE).
NSO Group admits that its real client list has over 40 countries on it, but in its defense, it says it vets the human rights records of clients. It also points out that the Pegasus malware “cannot be used to conduct cyber-surveillance within the United States, and no foreign customer has ever been granted technology that would enable them to access phones with US numbers.”
0-day vulnerabilities
All software has errors, known as bugs. It is a fact. It is also a fact that the number of bugs is directly proportional to the complexity of the software. More code means more bugs. Most bugs are just annoying. Something in the user interface that doesn’t work as expected. A feature that doesn’t work correctly under certain circumstances. The most obvious and annoying bugs tend to get fixed by the authors in small “point releases.” You find bugs in games, in operating systems, in Android apps, in iOS apps, in Windows programs, in Apple Mac apps, in Linux — basically everywhere.
Unfortunately, using open-source software isn’t a guarantee of a bug-free experience. All software has bugs. Sometimes using open source actually exacerbates the problem, as often key projects are maintained on a best-effort basis by a small group (or even a single person), who work on the project after getting home from their regular jobs. Recently three security-related bugs were found in the Linux kernel that had been there for 15 years!
And it is security-related bugs that are the real issue. The user interface has a glitch, it will get fixed, no problem. But when a bug has the potential to weaken a computer’s security, then the situation is more serious. These bugs are so serious that Google has a reward scheme that pays people who can demonstrate a security weakness in Android, Chrome, or Google Play. In 2020, Google paid out a colossal $6.7 million in rewards. Amazon, Apple, and Microsoft all have similar schemes.
See also: The best security apps for Android that aren’t antivirus apps
While the big tech names are paying out millions to squash these security-related bugs, there are still lots of unknown vulnerabilities lurking in the code of Android, iOS, Windows, macOS, and Linux. Some of these vulnerabilities are 0-day vulnerabilities — a vulnerability that is known to a third party, but not known to the software author. It is called a 0-day because the author has had zero days in which to fix the problem.
Spyware like Pegasus thrives on 0-day vulnerabilities, as do other malware authors, iPhone jailbreakers, and those who root Android devices.
Finding a 0-day vulnerability isn’t easy, and exploiting them is even harder. However, it is possible. NSO Group has a specialized team of researchers who probe and analyze every minute detail of operating systems like Android and iOS, to find any weaknesses. These weaknesses are then turned into ways to burrow into a device, bypassing all the normal security.
The ultimate aim is to use the 0-day to gain privileged access and control over a device.
The ultimate aim is to use the 0-day to gain privileged access and control over a device. Once privilege escalation has been achieved then the door is open that allows Pegasus to install or replace system applications, change settings, access data, and activate sensors that would normally be prohibited without explicit consent from the device’s owner.
To exploit the 0-day bugs an attack vector is needed; a way for the exploit to get a foot in the door. These attack vectors are often links sent in SMS messages or WhatsApp messages. Clicking the link takes the user to a page that carries an initial payload. The payload has one job: to try and exploit the 0-day vulnerability. Unfortunately, there are also zero-click exploits that require no interactions with the user at all. For example, Pegasus actively exploited bugs in iMessage and Facetime during 2019 which meant it could install itself on a phone just by placing a call to the target device.
Related: Is selling your privacy for a cheaper phone really a good idea?
One way to try and estimate the size of the 0-day problem is to look at what has been found, since we don’t know what has not been found. Android and iOS both have their fair share of reported security vulnerabilities. Publicly disclosed cybersecurity vulnerabilities are assigned a Common Vulnerabilities and Exposures (CVE) number. For 2020, Android chalked up 859 CVE reports. iOS had fewer reports, 304 in total. However, of those 304, 140 allowed for unauthorized code execution, more than Android’s 97. Four of the reports concerned privilege evaluation in iOS, whereas three of the reports were about privilege evaluation in Android. The point is that neither Android nor iOS are intrinsically secure and immune to 0-day vulnerabilities.
How to protect yourself from spyware
The most drastic, and the most impractical, thing to do is to ditch your phone. If you are genuinely worried about the prospect of being spied upon, then don’t give the authorities the access they are looking for. If you have no smartphone, Pegasus has nothing to attack. A slightly more practical approach could be to leave your phone at home when you go out or go to sensitive meetings. You would also need to make sure that others in your vicinity don’t have their smartphones either. You can also disable things like the camera on your smartphone, as Edward Snowden famously demonstrated back in 2016.
If that all sounds too drastic, then you can take some practical steps. However, you need to know that if a government agency is targeting you with malware like Pegasus, and you insist on keeping your smartphone, then there is little you can do to stop it.
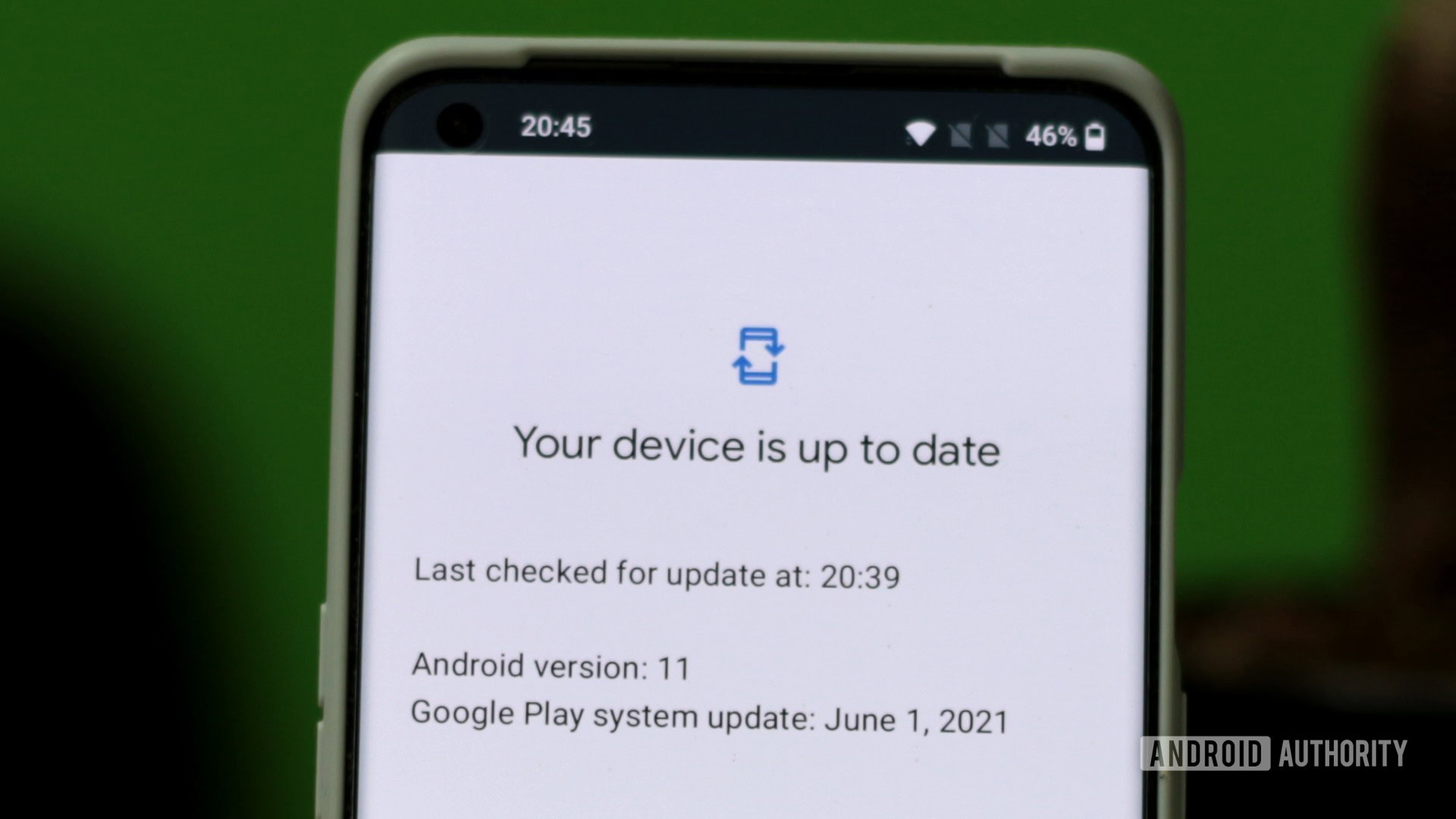
The most important thing you can do is keep your phone up to date. For Apple users that means always installing iOS updates the moment they become available. For Android users, it means first picking a brand that has a good history of releasing updates and then always installing the new updates the moment they become available. If in doubt pick a Google device, as they tend to get updates the quickest.
Secondly, don’t ever, and I mean never, ever, click on a link that someone has sent you unless you are 100% sure, without a doubt, that the link is genuine and safe. If there is even a slight doubt, don’t click it.
Thirdly, don’t think you are immune if you are an iPhone user. Pegasus malware targets iOS and Android. As mentioned above, there was a period in 2019 when Pegasus actively exploited vulnerabilities in Facetime that allowed it to install itself undetected on iOS devices. You might want to look at this video about how the Chinese government used vulnerabilities in iOS to spy on people.
Lastly, be vigilant, but remain calm and level-headed. This isn’t the end of the world (yet), but ignoring it won’t help either. You might not think you have anything to hide, but what about members of your family or your friends? Journalists, business executives, religious leaders, academics, and union officials aren’t such a rare bunch that they have no friends or family. As the World War II slogan said, “Loose lips sink ships.”