Affiliate links on Android Authority may earn us a commission. Learn more.
The NSA's catalog of spy gear shows how it hacks computers

Although the catalog is over four years old it contains a remarkable array of gadgets and we can all be sure that the NSA hasn’t been idle. If four years ago the agency could create an implant that sits within the physical Ethernet/USB stack that is found on so many motherboards, imagine which little devices it has now that can be implanted into smartphones and tablets! Replacement batteries with bugging devices, hidden RF transmitters or what about SD cards with NSA implants?
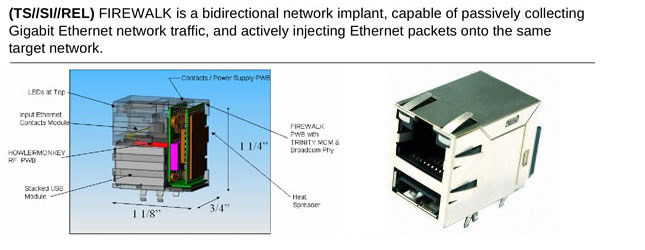
The Ethernet implant, which is called FIREWALK, was designed to collected network traffic and inject Ethernet packets into the target network. But it is only one of a bewildering range of gadgets used by the NSA. The ANT unit of the America’s National Security Agency has USB sticks that act as listening devices and portable cellular base stations that can intercept every call and SMS message from your phone.
But here is the really interesting part, the NSA has working spyware that implants itself into the BIOS of PCs. The BIOS is that bit that shows the graphic of your PC maker, or maybe some white text on a black background, that appear briefly before the Windows logo is displayed. It is the lowest level of software that runs on a PC and is stored on flash memory on the motherboard. From time to time motherboard makers release new versions of the BIOS software for their motherboards to fix bugs. This means that consumer level tools exist to replace the firmware with the latest version. So this is consumer level tech used in a nefarious way.
Now imagine a situation where the NSA sends in a undercover engineer to perform a BIOS upgrade on a PC with spyware pre-built into it. Or where the agency intercepts that new motherboard you just bought online and installs its own BIOS before repackaging it and posting it on to you. Or worse imagine a situation where the NSA has managed to alter the official BIOS of a motherboard, either by coercion, bribery or subterfuge, so that the official BIOS on a motherboard actually contains NSA spyware.
According to Spiegel ANT also has spyware capable of embedding itself unnoticed into hard drives manufactured by Western Digital, Seagate and Samsung.

This was all four years ago. Now imagine what the NSA can do with a smartphone! It isn’t hard to imagine how the NSA can create versions of Android with its spyware cooked into it and then when it wants surveillance on someone it arranges an upgrade for the phone which looks and behaves exactly like the clean version of Android. Or what about bootloaders? There are some fairly sophisticated bootloaders out there now which are used for managing custom ROMs. What if the NSA can replace the bootloader on your device with one that can spy on you?
Speigel make it clear that it has not seen any documents which suggest that equipment manufacturers are in anyway connected with this spying, but rather these devices are the sole work of the NSA in its attempts to spy on people.
What do you think? Are the revelations a shock or should we all have assumed that this was what the NSA was doing all along?