Affiliate links on Android Authority may earn us a commission. Learn more.
iOS 16.5.1 fixes critical iMessage security flaw, you should update immediately!

- Apple is rolling out critical security updates to iOS 15 and iOS 16, patching an iMessage flaw that was used to plant spyware on iPhones.
- The exploit was used on iPhones running iOS 15.7 and earlier. iOS 16 had other changes that protected it from this cyberattack.
- iPhone and iPad users are recommended to update their devices immediately.
Update: June 22, 2023 (10:14 AM ET): An Apple spokesperson told Android Authority that there was no sign of this exploit being successfully used against devices running iOS 15.7 or later.
The spokesperson did, however, note that Apple released critical security patches to address other elements of the exploit so they couldn’t be harnessed for separate attacks.
Original article: June 22, 2023 (5:02 AM ET): Apple prides itself on the security and privacy provided by iPhones, and to a good extent, we do agree that it is better than Android. However, iPhones are relatively secure, and not absolutely secure. The proof for this assertion lies with the new iOS 16.5.1 update that is rolling out to iPhones, bringing an urgent fix for a critical iMessage security flaw. If you own an iPhone, we strongly recommend updating your phone right away.
Apple is rolling out iOS 16.5.1 and iPadOS 16.5.1 to users. The primary fix mentioned in the changelog is a fix for an issue that prevented charging with the Lightning to USB 3 Camera Adapter.
However, the changelog also mentions “important security fixes,” which are highlighted in a separate document. These two security flaws pertain to the “Triangulation” cyberattack that was highlighted by Eugene Kaspersky, the CEO of Kaspersky, earlier this month.
As The Washington Post mentions, the security flaw was used to hack thousands of devices, including those of Kaspersky’s senior employees.
The Triangulation attack worked by sending an iMessage with a malicious attachment. The user does not need to see the message or even open it for the spyware to be planted on the iPhone.
The spyware then transmits private information such as microphone recordings, photos from IM apps, geolocation, and other data to remote servers. It can even extract passwords from Apple’s keychains, and modify and export files.
The security flaw is separate from past iOS exploits such as Pegasus, Predator, or Reign. Among other ways, it is different from these as there are a few ways to already protect yourself.
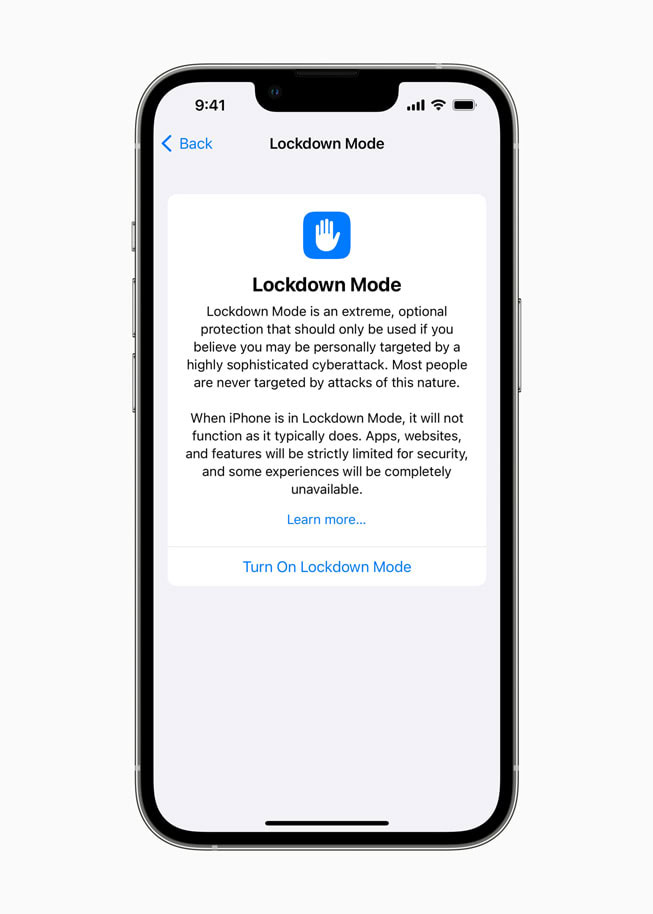
One, disabling iMessage would prevent your phone from being infected. Two, since the spyware in this instance resides in the memory of the iPhone, simply turning an infected iPhone off and on again would “cure” it from the spyware (until it gets re-infected). Third, Apple also has an optional Lockdown Mode available in iOS that would block the attack.
In The Washington Post‘s report, Apple claims that the attacks were only possible on iOS 15.7 and earlier, as newer versions of the OS had other improvements that would make them impervious to the attack. Further, 90% of customers who bought devices in the past four years had already updated to iOS 16.
For users who do not want to (or cannot) update to iOS 16, Apple is also rolling out iOS 15.7.7 and iPadOS 15.7.7 which include the same security fixes present on iOS 16.5.1 and iPadOS 16.5.1 respectively.
If you own an iPhone or iPad, we strongly recommend that you update your device to the latest software update available for your device. If you need assistance, follow our guide on how to update your iPhone to the latest iOS version and how to check the iOS version on your device.
We’ve reached out to Apple for a comment. We’ll update the article when we hear back from them.