Affiliate links on Android Authority may earn us a commission. Learn more.
Video: Bypassing Factory Reset Protection on Nexus devices is still stupid simple
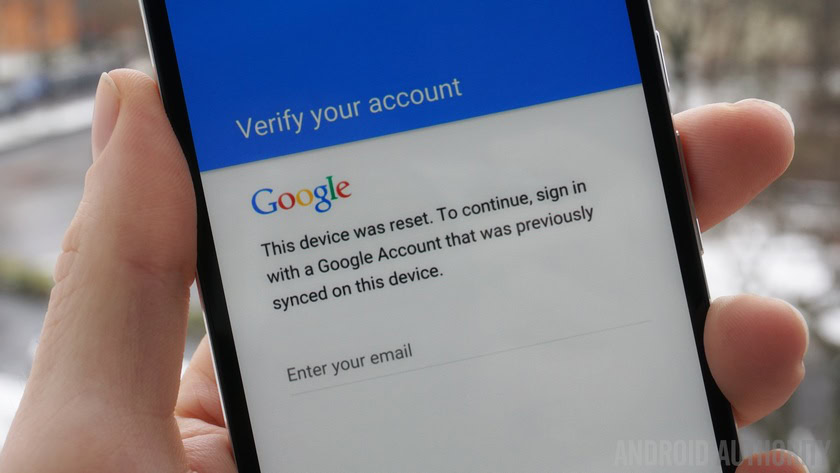
If you can tap on a screen and follow simple instructions, you too can “hack” into a Nexus device that, in theory, should be secured by Factory Reset Protection.
Back in March, we reported on how easy it was to bypass Factory Reset Protection using a simple exploit uncovered by RootJunky. The exploit, technically known as an “escalation of privilege” involved using various menus, search bars, and other features of the stock Android interface to reach the Settings menu. Once there, anyone could add a new Google account and factory reset the device. FRP completely failed to do its one job.
Since March, Google has patched that specific exploit, but as it turns out, RootJunky found a different workaround pretty fast.
The new exploit works on Nexus devices running Marshmallow or Android N, including Nexus 6P, Nexus 5X and Nexus 6, with the May security patch applied. (The patch that was just released earlier this week.)
As you can see from the video below, the new exploit involves more steps (including downloading and installing a special app), but it’s fair to say that anyone who has a basic knowledge of using Android can successfully bypass FRP in a few minutes.
What’s more worrying is the apparent ease with which RootJunky (and presumably other, less savory, characters from around the web) can render FRP useless. Not only that, but Google seems content to patch each exploit as it surfaces, without addressing the root issue, a year after this security-critical feature was first introduced.
Let us know your thoughts.