Affiliate links on Android Authority may earn us a commission. Learn more.
Quadrooter: the latest Android security flaw
Original post, August 8: Welcome back for another episode of “Android malware daily”. In today’s episode, the sinister Quadrooter vulnerability puts a billion Android devices at risk and won’t be fully patched until the September security release. The flaws appear in the drivers for Qualcomm chipsets – so, a vast majority of Android devices – and could potentially allow a hacker to take over your device completely. But don’t go stockpiling canned goods and barricading the basement just yet.

What is Quadrooter?
Yet again it’s a privilege escalation vulnerability, the kind that would allow a hacker that manages to dupe you into installing a dodgy app – say a side-loaded version of Pokémon Go or the new Nexus Launcher – to then gain root access and take control over all aspects of your phone, from GPS and data to camera and microphone.
As the researchers that uncovered the flaw report:
An attacker can exploit these vulnerabilities using a malicious app. Such an app would require no special permissions to take advantage of these vulnerabilities, alleviating any suspicion users may have when installing.

Qualcomm’s response
Qualcomm distributed fixes for its drivers to its various partners and the open source community between April and the end of July. While three of the four vulnerabilities were addressed in Google’s August security update, one has been delayed until the September patch.
While some devices including the Nexus line receive these patches lickety split, other devices have to wait months to get the latest security fixes. It is possible that individual OEMs will issue their own patches for the Quadrooter flaws before Google’s next security update, but I wouldn’t hold your breath.
In the meantime, the security researchers that uncovered the vulnerability recommend a few general security measures including not installing apps from outside Google Play, being vigilant with permission requests and always installing the latest updates from your carrier or manufacturer.
The real issue
So while the chances of being affected by Quadrooter are very slim, the risk is there, as it always is with these big attention-grabbing vulnerabilities. But remember that exploits like these very rarely generate any real-world victims.
Perhaps the more important part of these stories is not that your phone might be affected, but that they force the security discussion into the spotlight. As Check Point correctly surmises:
This situation highlights the inherent risks in the Android security model. Critical security updates must pass through the entire supply chain before they can be made available to end users. Once available, the end users must then be sure to install these updates to protect their devices and data.
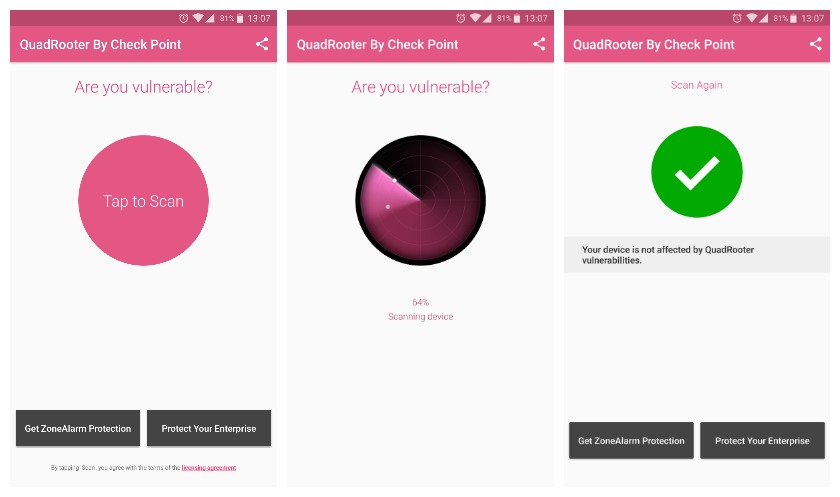
The inevitable app
As always, there is an app available to see what Quadrooter flaws your device is vulnerable to. But other than arming yourself with knowledge there is not much the app or you can do until the patches roll in. If you’re interested, you can also download the report on Quadrooter from Check Point if you want to know more.
While hoping that Android security will suddenly become watertight and universally supported is a bit of a chimera, we can all play our part. Support those manufacturers that take security updates seriously, adopt best practices when installing apps, pay attention to permissions and so on. Until we can all say we do our bit, Android will continue to be an easy target for bad actors.
What security patch are you running? Do you think the Android security model needs addressing?