Affiliate links on Android Authority may earn us a commission. Learn more.
Google will pay up to $8000 to researchers disclosing Android vulnerabilities

Google is extending its bug bounty program to cover vulnerabilities found on Android devices sold through its store.
The new Android Security Rewards program covers vulnerabilities found on current Nexus phones and tablets that are available in the Google Store (formerly, the hardware section of Play Store). Currently that means the Nexus 6 and the Nexus 9. The program supplements Google’s other bug bounty schemes, such as the Patch Rewards program, which launched in 2013 and includes AOSP and many other projects.
“Eligible bugs include those in AOSP code, OEM code (libraries and drivers), the kernel, and the TrustZone OS and modules. Vulnerabilities in other non-Android code, such as the code that runs in chipset firmware, may be eligible if they impact the security of the Android OS.”
Google will only reward the first reporter of a specific bug, with bounties varying based on the severity of the issue, and whether or not the reporter offered a test case and/or a fix for the vulnerability.
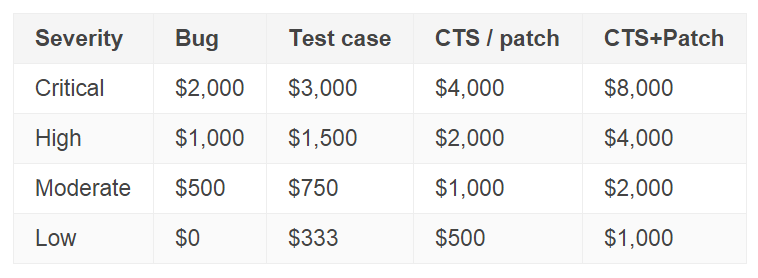
For verified exploits that can lead to the kernel or boot being compromised, Google is willing to raise the bounty by up to an extra $30,000. The company will match any bounty that reporters opt to donate to a charity of their choosing.
Google launched its first bug bounty program in 2010, and since then, it paid $4 million to researchers, with $1.5 million in 2014 alone.
Installed on four out of every five smartphones in the world, Android has become the primary target of mobile malware developers, though the security measures implemented by Google ensure that only a very small number of malware-ridden apps compromise user devices. But it’s not just malware that Google worries about – a recent report revealed that the NSA was very interested in using the Play Store to surreptitiously deliver spyware on target devices, though it’s not clear what came of that program.
Unfortunately, Google’s efforts alone are not enough to ensure that bugs are exterminated in a timely fashion. Carriers and OEMs have the power – and responsibility – to deliver security patches for most devices, but time and again, they proved uninterested in doing the right thing for the customer.