Affiliate links on Android Authority may earn us a commission. Learn more.
What is a passkey, and how does it work?
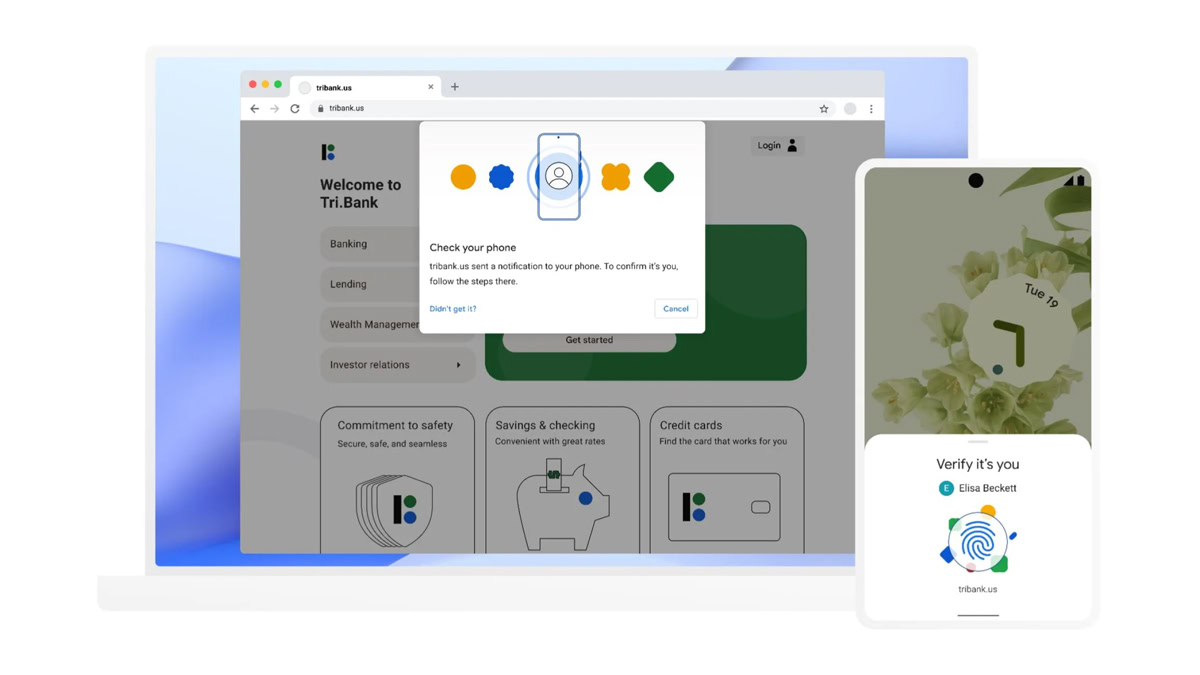
If you’ve been paying attention to cybersecurity lately, you’ve probably heard mention of passkeys. Google is already rolling them out, and they may be poised to change how we secure the internet — but what are passkeys, exactly? And are they any better than the password logins we’ve been using for decades?
What is a passkey?
Passkeys are all about ditching password logins to avoid their weaknesses (more on those later). Instead, an authenticator such as a phone OS keychain or a separate password manager generates a pair of cryptographic keys, granting you access to other apps and websites. You still need to verify your identity through the authenticator, of course, which probably means a master password, with optional facial or fingerprint recognition to speed things up.
An important aspect of the passkey concept is portability. It’s potentially very easy to sync passkeys between your devices, as long as you have that master password to get things unlocked.
How does a passkey work?
When you enable passkeys within a compatible app or website, your authenticator creates a set of public and private cryptographic keys. For secure authentication, those keys are exchanged, encrypting traffic against the outside world.
Public keys are called that because they’re stored on servers associated with an app or website. A hacker can hypothetically breach a server and steal your key, but without your master password and your private key, it’s effectively useless.
Private keys are always saved locally on your devices, and supplied to servers only when something demands credentials. You have to verify your identity for the process to complete. Note that a server doesn’t need the full details of a private key, since there’s a mathematical link with its public equivalent.
Passkey vs password: Which one is more secure?
Passkeys are generally more secure, since passwords inevitably have to be saved in a remote database. Though many companies have defenses in place, a skilled hacker can potentially breach them, and any logins they find are immediately useful if they’re not backed by two-step verification (2SV). The situation is made worse when people reuse passwords too often — hackers may not need to bother with other servers if the same password works everywhere.
Human nature can defeat passwords in other ways. Often we don’t put enough thought into them, making them easy to guess or brute-force through repeated attempts. When that’s not a problem, we sometimes share them with people we shouldn’t, say if we’ve fallen prey to phishing scams.
Passkeys aren’t invincible, naturally. If someone gets a hold of one of your authenticators and your master password, they may have the keys to your entire digital life, or least everything that uses a passkey. That should be less likely than attacks on remote servers, however.