Affiliate links on Android Authority may earn us a commission. Learn more.
Worried about Stagefright? Here's what you can do for now
Android vulnerabilities have been surfacing regularly over the past couple of years. They stir up talk – usually some rather alarmist posts by security companies and a flurry of comments on various tech blogs. But then something interesting happens – the scares just fade away, replaced by other alerts, to the point that worrying about (in)security has become the norm in the Android ecosystem.
Stagefright appears to be different. The vulnerability affects 95 percent of all Android devices, and can be exploited with a simple MMS message. A specially designed piece of malware could spread like wildfire by tapping into the contact list of every infected device. Perhaps that’s why Google and major Android OEMs have actually tried to offer a coordinated response.
There’s a very long and very complex discussion to be had about the root of the evil in the Android ecosystem. But that’s not the point of this post. For now, you will probably want to check if your device is vulnerable to Stagefright-based exploits.
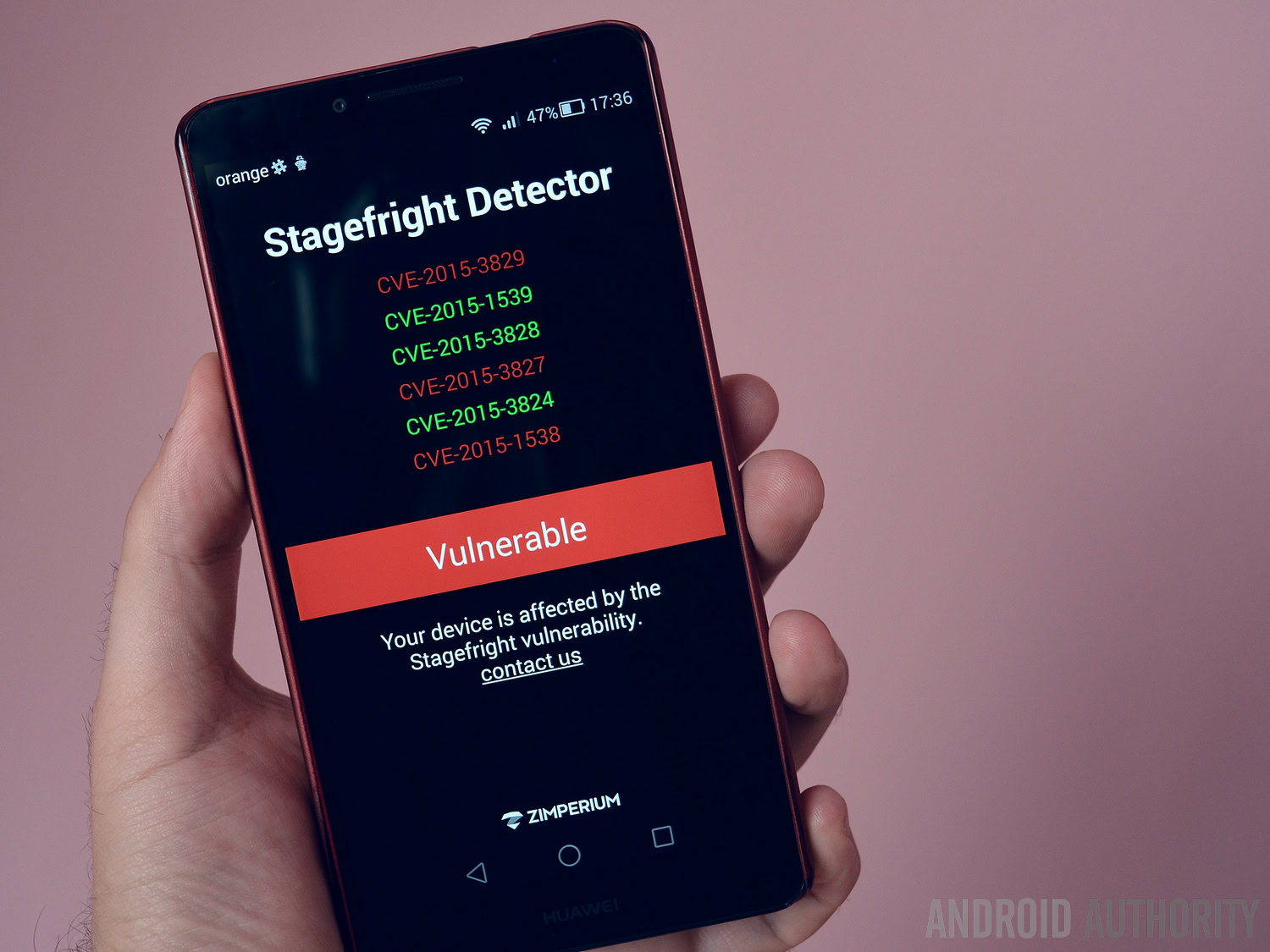
Zimperium, the company that discovered Stagefright, published a simple app that checks if the device is exposed to any of the several vulnerabilities that make it up. Simply install it, tap “Begin Analysis,” and the app will show which vulnerability affects your phone. Unfortunately, the app does nothing else, so it’s up to you to look up what each code means and what you can do about it.
So, what exactly can you do if your phone has a case of Stagefright? First up, don’t panic. There is no exploit of this vulnerability in the wild, as far as we know. And there are a few simple things you can do to protect yourself.
- Disable the auto-retrieval of MMS, as the vulnerability relies on modified videos embedded in MMS messages. Some apps auto-retrieve MMS content before you open it – you don’t want that, because that can get your phone infected without you even knowing it.
- Consider switching to a messaging app that has been updated with some level of protection against Stagefright, like Textra.
- Consider switching to a custom ROM like CyanogenMod – the latest CM nightlies are patched against Stagefright.
- If you’re particularly worried about this issue, don’t open MMS messages from unknown numbers.
- Update your messaging apps and check for updates for your device. Google, Samsung, LG, HTC, Sony, and others have promised patches for their main devices. Unfortunately, the majority of smartphone models will remain unprotected, unless the industry does something radical to change itself.
- Again, don’t panic. The risk is minimal at this point, so you shouldn’t lose any sleep over it.
There is something you can do so things change for the better in the Android ecosystem. Call your manufacturer. Call your carrier. Ask about updates and security patches. Perhaps if thousands of customers speak up, they won’t be able to ignore the issue any more.