Affiliate links on Android Authority may earn us a commission. Learn more.
Android malware uses phone motion sensors to hide itself

In the movie Batman Begins, Commissioner Gordon lectures Batman on how his theatrical persona will likely lead to the same kind of escalation from the bad guys of the city. As good as Batman might be, he does set the bar higher for a harder class of criminal.
A similar escalation is happening within Android malware: as security researchers and the Google Play Store itself get better and better at tracking and stopping Android malware, the malicious coders who create the malware get better in turn.
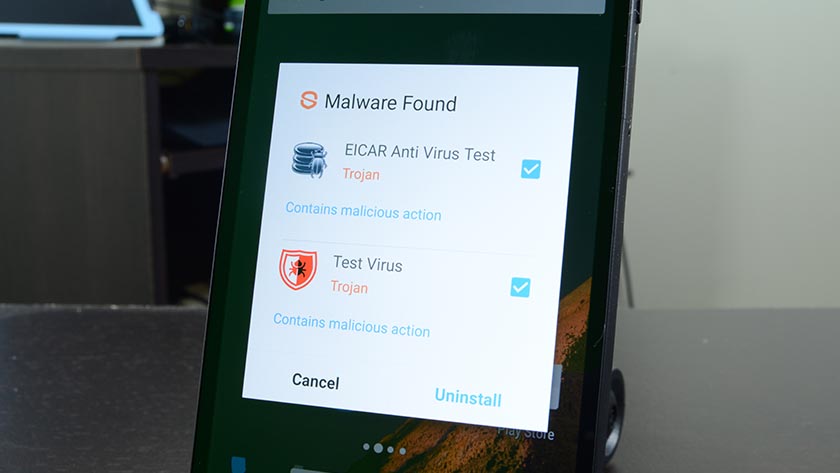
Case in point: there are now malware-infested apps that only deploy the malware when the software detects motion from the smartphone, via ArsTechnica. The reason for this is that most security research teams use Android emulators to test for malware — i.e., not real smartphones. The emulators are not coded to emulate motion by default because most would think that wouldn’t be necessary. As such, the Android malware slips through those emulation systems undetected but will deploy on a real smartphone without issue.
This ingenious workaround was recently discovered by Trend Micro in two apps — BatterySaverMobi and Currency Converter. Both apps are no longer on the Google Play Store.
Luckily, the BatterySaverMobi app had less than 5,000 downloads, so the damage is likely minimal.
Since malicious coders are getting better at hiding malware from security detection, it is more important than ever to ensure you are only downloading apps from the Google Play Store that you trust. When in doubt, try to find the app with the highest number of downloads and/or reviews, as they will likely be safer than apps with a small number of users.
NEXT: 15 best antivirus apps and best anti-malware apps for Android!