Affiliate links on Android Authority may earn us a commission. Learn more.
Can Android Be Used As a Pentesting Platform?

Have you ever wanted to dabble in network security testing? How about to test the security of your own network? The Android Operating System is the perfect platform for mobile pentesting applications. What is pentesting, you may wonder? Pentesting stands for penetration testing, and is the practice of testing a computer system, network or web applications for potential vulnerabilities that can be exploited. Sounds cool, right? Read on.
This article is technical in nature, and only serves as an information guide for people curious to maximize the utility of their Android device. If you choose to pentest with your Android device, keep it legal, and only do it on networks that you own, or have permission to access.
It is public knowledge that Android is based on a Linux kernel which allows for a large amount of modification. In fact, Linux is already commonly used for network pentesting and has been for many years now. In order for pentesting to work, the Android device would definitely need to be rooted, but with the right software, any Android device could be a lethal hacking tool.
There doesn’t seem to be any exception to the statement that every Android device has WiFi. After you root an Android device, you have as much software-based access to the device as is currently available, so that means you can do whatever you want with the wireless interfaces of the device. At least a few developers are publically known to be working on modifications for Android devices that would enable the functionality I’m speaking of.
An example of one pentesting platform that showed promise is Zimperium’s ‘Anti’. Anti offers OS detection, WiFi monitoring, exploitation of vulnerabilities, etc. Unfortunately Anti uses a token system that would just plain drain the average wallet.
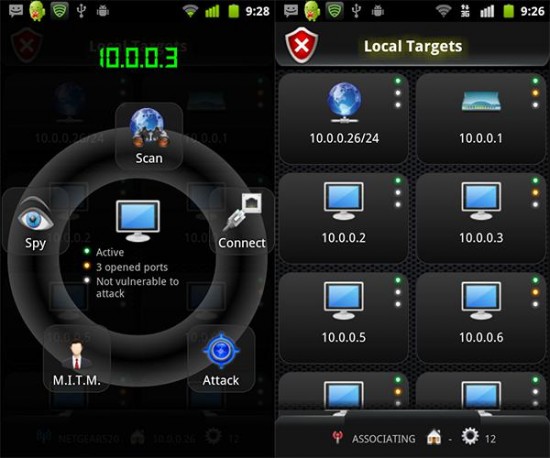
There are other tools focused on wardriving, cracking, and analyzing wireless networks available for Android phones but it seems there is a lack of full on free applications with which to actually exploit vulnerabilities of target machines. This issue could be solved by making new programs for Android phones with these functions, installing a new OS in dual boot using SGS2 Dual-Boot Setup or another tool, or by porting already existing Linux programs to the Android OS.
Porting existing programs seems to be the best option. One reason for this is that you would not have to learn new tools if you have experience with pentesting on a laptop or desktop computer. Another reason is that if you use a program that is already well suited for its task, you only have minor problems to worry about (unlike building from scratch). Lastly, Android is already Linux based and there is very little that stands in your way if you wanted to make Linux command line tools designed to run on Android.
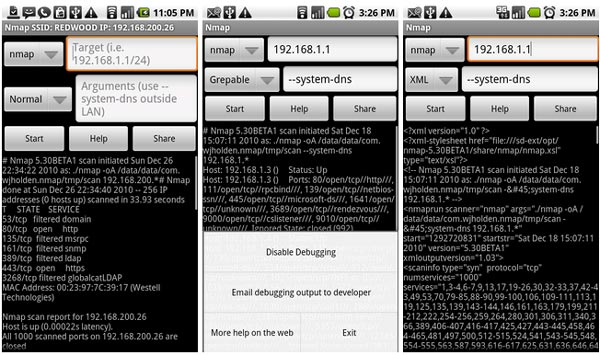
Nmap is one tool that would be essential in such a toolset. Nmap is an application with a command line interface(CLI) and an optional GUI that scans a potential target for network vulnerabilities. Due to Nmap’s CLI, as soon as it’s prerequisites are met on the device, Nmap should work just fine.

Another tool that would be useful to port would be Aircrack-ng. Aircrack-ng is commonly used for cracking wireless network passwords. It does this by monitoring wireless communications and using the information it gathers from the captured packets. Aircrack is primarily a command line program and could be quite simple to port. Aircrack-ng would simply need to be allowed to access the device’s wireless hardware and have all prerequisites installed.

The next tool an Android pentesting system could use is a Bluetooth capture tool. Kismet is a command line tool that allows raw packet capturing on many interfaces including Bluetooth, and WiFi. Another feature of Kismet is that you can install plugins that allow for raw capturing on more interfaces. Kismet could be a useful program to include in this Android Pentesting Suite.
THC Hydra could also come in handy. THC Hydra is a command line based tool for network login hacking with an optional GUI. THC Hydra can crack passwords using bruteforce or it can try to see if the password is in a wordlist. This tool could prove useful when attempting to get access to a server located somewhere on the internet. Hydra is an essential inclusion in a pentester’s arsenal.
Yet another tool to include is John the Ripper. John the Ripper is another login cracking tool which would be very useful for privilege escalation on a computer you already have access to but need higher access priveleges for what you wish to do. John the Ripper is command line based and as with the others should not be difficult to install on an Android device.
All of these tools, when developed, could easily make Android devices into the next great hacking tool. Any thoughts?