Affiliate links on Android Authority may earn us a commission. Learn more.
What is root - Gary explains

You may have heard of the term “rooting your phone” and you may have seen that some apps on the Google Play Store require “root” access to work. But what is root? What is “rooting” your phone and why would you do it? Let’s find out!
The majority of operating systems including Windows, OS X and Linux have the concept of system privileges where processes, and therefore users, run at different privilege levels which determine what the process is allowed or prohibited from doing. On some OSes this scale of system privileges is fine grained with a range of privileges from the lowest to the highest. On Unix-like operating systems the difference between an unprivileged user and a privileged user is more black and white. A process or user is either unprivileged, or privileged, with no ambiguity in between. A privileged user on Linux is known as a superuser or root.
There are certain things that root can do that normal users can't do.
There are certain things that root can do that normal users can’t do. The most important of which is that root can access any file, anywhere on the system. A normal user is limited to accessing their own files and files within their assigned groups. This is quite sensible, on a multi-user server, your files are yours and you don’t want others snooping around. It also means that normal users can’t go around altering system files. If they could then there would be havoc.
su
As you can imagine the fact that root access exists doesn’t mean that it is granted automatically to every user or process. To gain root privileges a process or user must ask for it. On Linux this is handled in one of two ways, either with the su command or the sudo command. The first one means substitute user and it basically allows a process to substitute its current user id for that of root and gain the privileges associated with being root. The second is similar but applies to just one command, “do with a substitute user” or basically “do as root.”
On systems which use su you need to know the password for the root account, so basically root access is off limits to those who don’t know the password. With sudo things are a little different and depending on how the system is setup, you need to be an authorized sudoer and/or you need to authenticate with a password. So su and sudo ensure that there is an authentication step needed, so that only those allowed to have root access actually gain it.
Root access
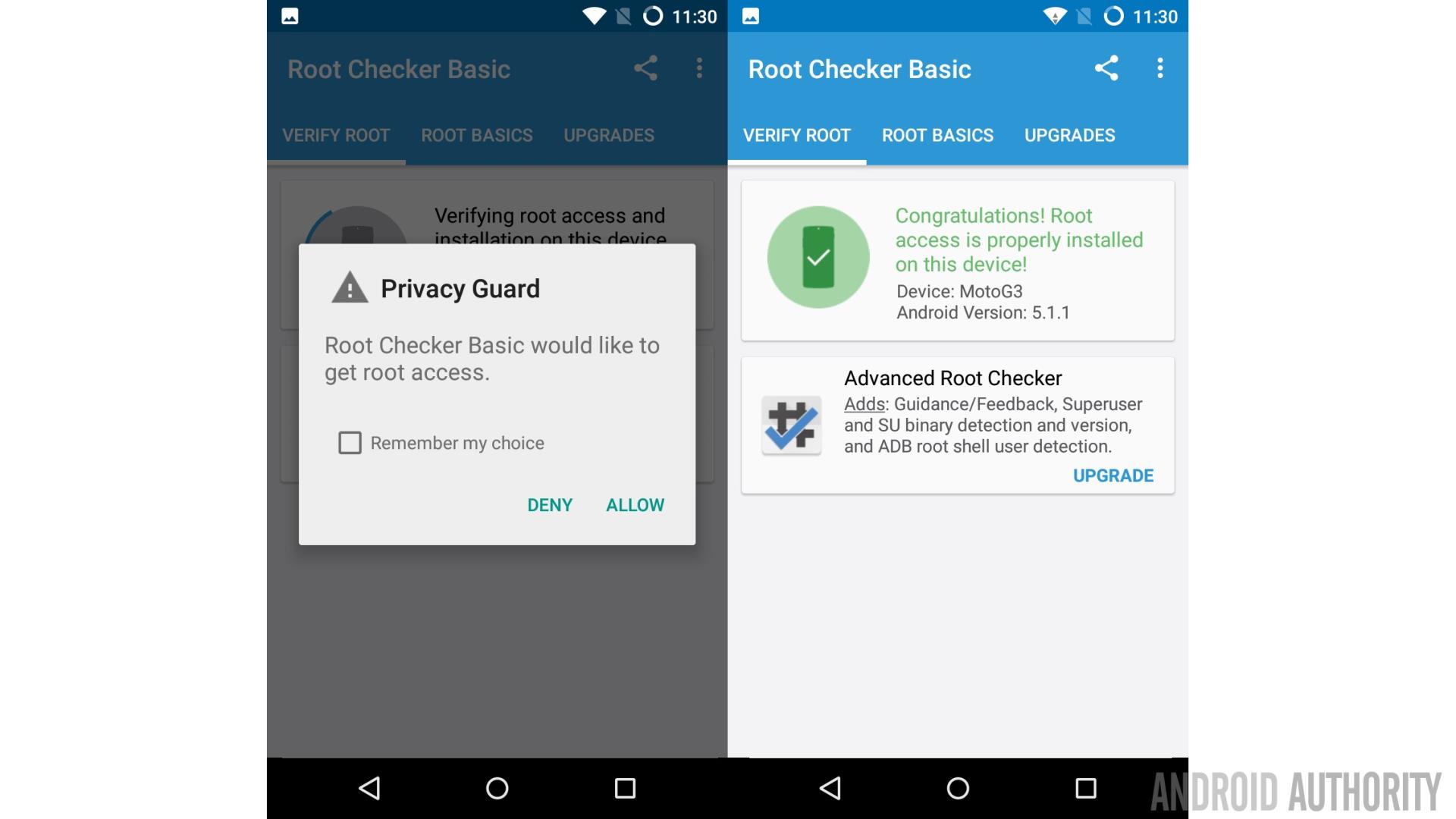
Now let’s apply that theory to Android. Our favorite mobile OS runs on top of a Linux kernel. That means that there are normal processes and there are root processes. It also means that normal apps can’t go around altering the system files or snoop around in the data of other apps.
But on Linux (and other Unix-like operating systems) when a process or user gains root access, they can do everything including altering system files and reading everyone’s data. The same is true on Android, an app that can gain root access can alter the system and it can see all the data belonging to other apps. As you can imagine this could be equally a benefit and a security nightmare.
It is a benefit as it means that app developers can create apps which perform privileged operations, actions that would normally be prohibited. One of the most popular root apps is Titanium Backup root which allows you to backup your apps including all protected and system apps, something it wouldn’t be able to do without root access.
However, Google has invested a lot of effort in making sure that Android is as secure as possible. Like all operating systems (including iOS) there are bugs which can be exploited (and we will talk more about that in a moment). But the downside of having root access available on your device is that any app can seek to gain root privileges and if it succeeds then it can do anything it wants, including stealing all your private data.
This isn’t as hard as you might think. I could write a free little game that looks harmless enough and on non-rooted devices it will remain harmless. But the moment it sees that root access is available it will try and convince the user to grant it root privileges. It could try in a variety of ways including lying about downloading updates, improving speed or memory usage, needing root access to upload the scores and so on. The moment an unwary user grants it root access then BAM! Everything is exposed. That is why it is best to keep this door firmly shut.
How to get root access
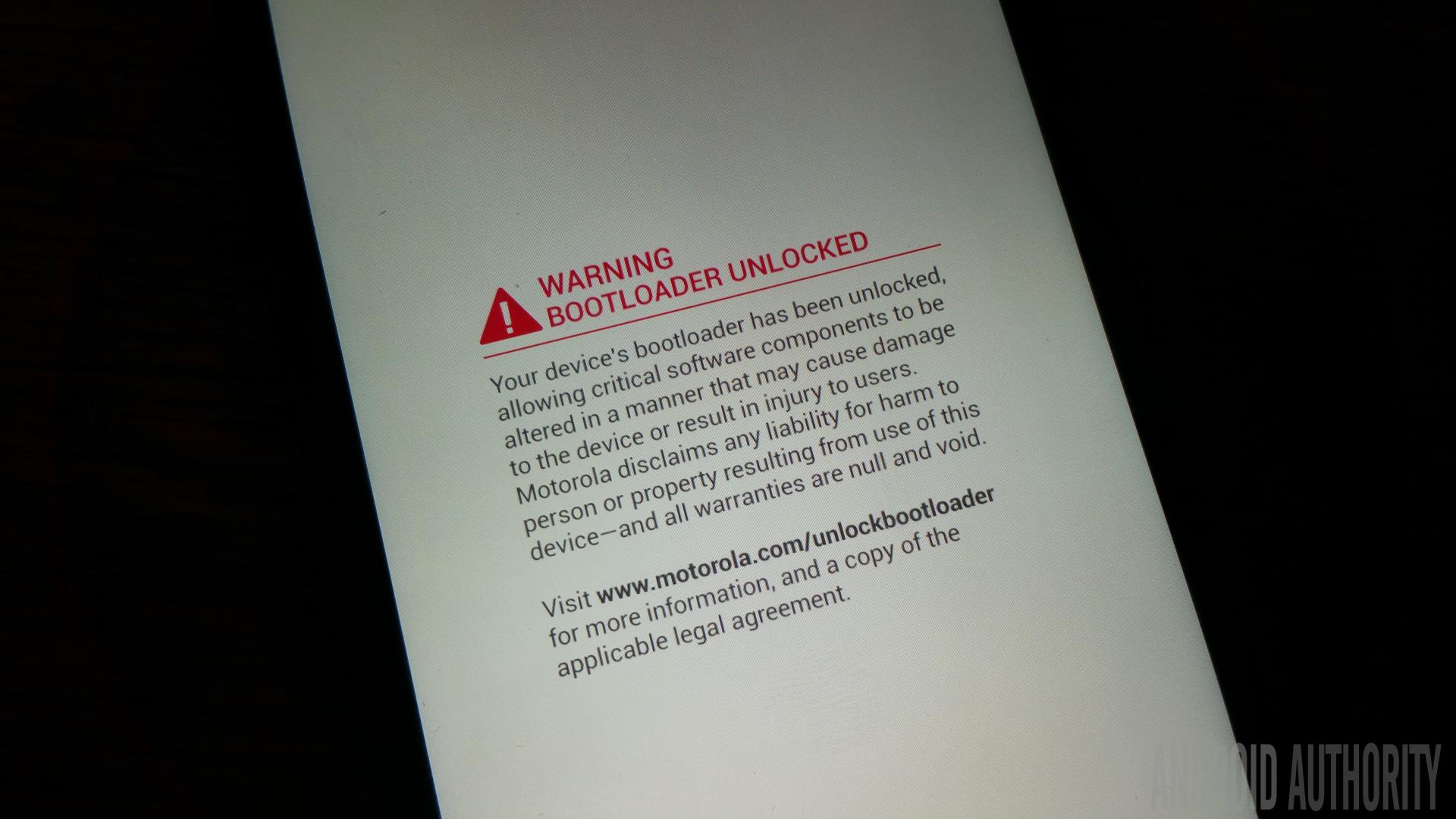
As you have probably guessed root access isn’t available on the majority of retail Android phones. The occasional device from China might come with root access enabled but overall it isn’t something you can expect to find by default. There are several different ways to get root access on your phone, and it really depends on which phone you have. Some phones can be rooted just by replacing the boot loader and then adding some special su files, while others need to use an exploit. A third method is to install a custom ROM like Cyanogenmod, which has root access pre-baked into the software. Which method is best for you really does depend on your device.
I mentioned earlier that all operating systems have bugs, in security circles bugs which could potentially allow for security breaches are called vulnerabilities, and an actual piece of code which uses a vulnerability is called an exploit. For some phones to be rooted a vulnerability needs to be exploited. What basically happens is that due to a bug some code can be crafted to run at an elevated privileged (i.e. root) and using root the relevant su files can be copied onto the phone to grant permanent root access, without having to constantly exploit the vulnerability. These rooting methods often only work for certain firmware versions as whenever Google or Samsung or whoever find out about these vulnerabilities they are patched and the code fixed.
Wrap-up
To recap – root is the most powerful user in the Linux world. Root can do anything include changing the system files. Android uses a Linux kernel and so the concept of root exists on Android devices. A phone is considered “rooted” when normal apps have the ability to raise their privilege levels to that of root. Although root access has its advantages, in that root apps can do more than “normal” apps, it does present a security risk.