Affiliate links on Android Authority may earn us a commission. Learn more.
Will Google's Titan M make it harder for the ROMing scene?

Google talked up the security of its new Pixel 3 and Pixel 3 XL smartphones during its launch event, which all centers around the new Titan Security feature packed into the handsets. Titan Security hinges on Google’s new custom-built Titan M security chip.
The Titan M is Google’s second generation security module, this time designed for lower power applications like phones. The first generation Titan chip was designed for Google Cloud data centers. Let’s delve deeper into what the chip can do and what it means for Google’s latest Android flagship.


A closer look at the Titan M
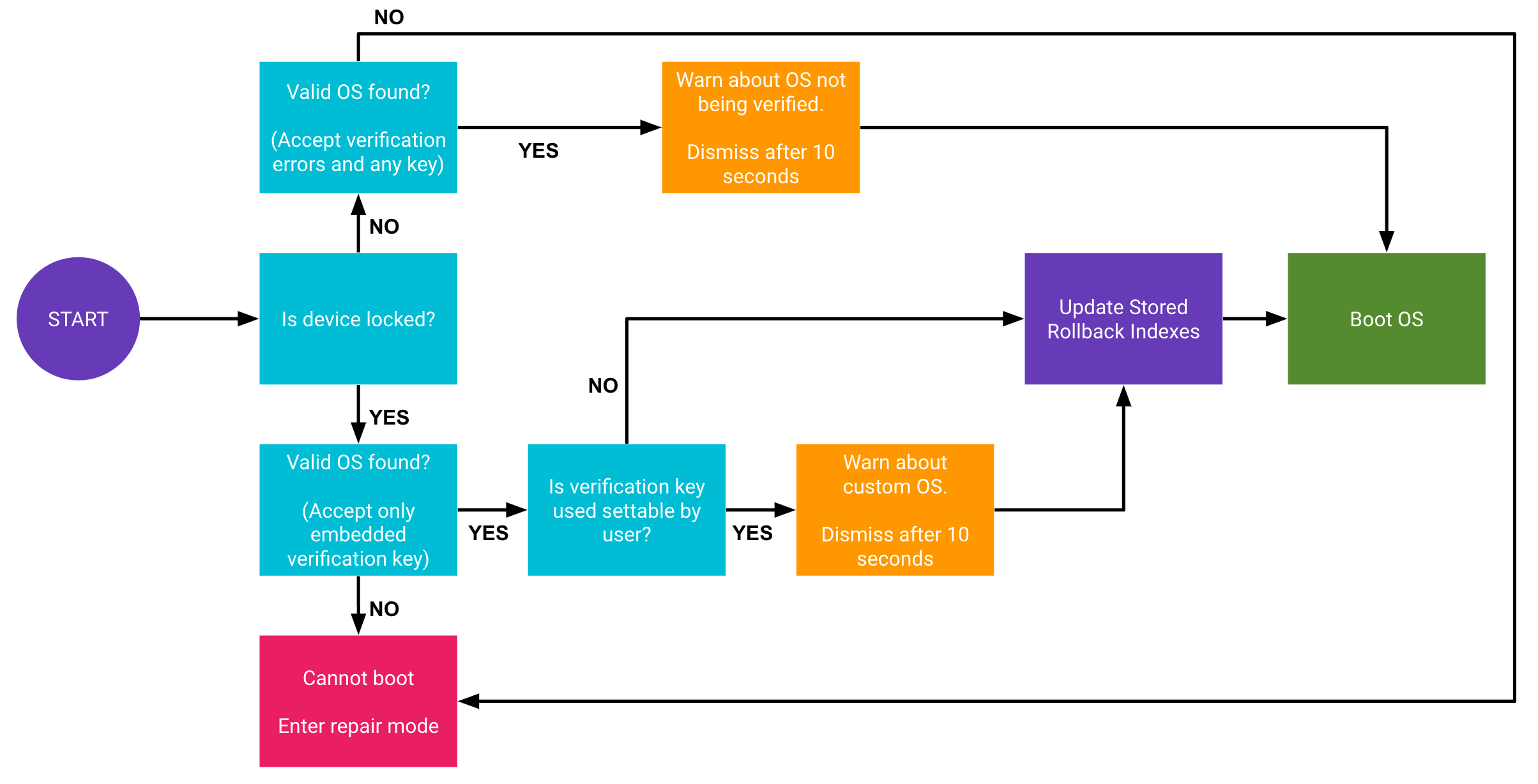
At its most basic level, Google’s Titan M is a standalone security focused chip that sits alongside the main processor. In the Pixel 3’s case, it’s paired up with the Qualcomm’s Snapdragon 845. The chip’s primary function is to verify the boot conditions for starting up Android, ensuring that it hasn’t been tampered with at a low level. The Titan M verifies the signature of its flash-based firmware using a public key built into the chip’s silicon.
In other words, there’s now a separate hardware component to Android Verified Boot in the Pixel 3, which is an updated Project Treble compliant version of Verified Boot that has been around since Android 4.4. Or as Google puts it, the chip is designed to “make sure that you’re running the right version of Android.” Another way the Titan M does this is by preventing code from unlocking the bootloader, meaning that malware can’t gain access to the lower software-levels of your device. It also won’t allow malicious attacks to rollback Android to an older, less secure version.
On top of this, the Titan M handles the Pixel 3’s lock-screen passcode verification, stores private keys for Android 9’s StrongBox KeyStore API, and prevents firmware updates without the correct user passcode. The chip also supports the Android Strongbox Keymaster module, including Trusted User Presence and Protected Confirmation, which can be exposed for verification to third-party apps through FIDO U2F Authentication and other means. In other words, the chip can be used as a safe storage space for payment and app transactions too.
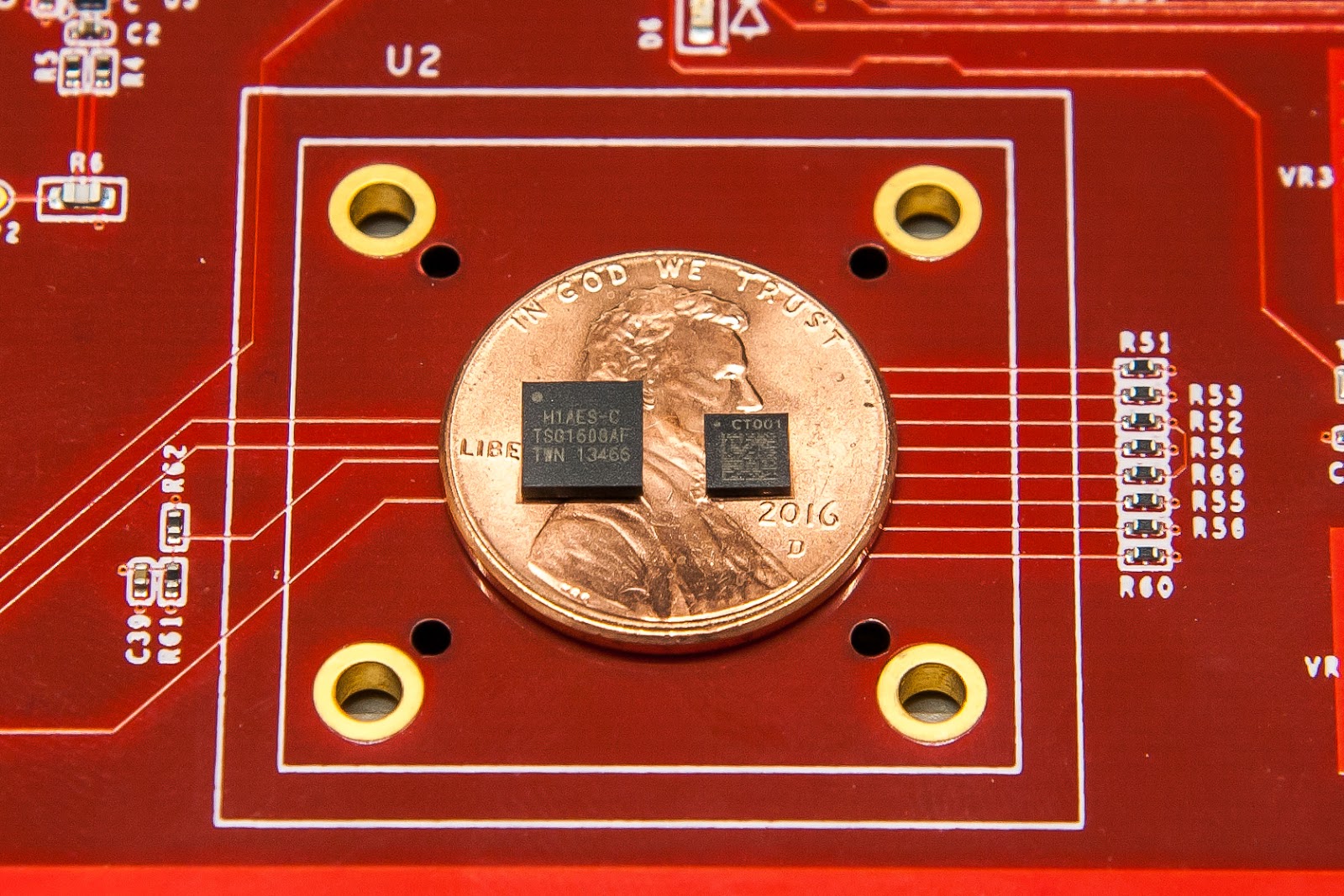
Google states that the Titan M features a low power ARM Cortex-M3 microprocessor. The SoC has been specially hardened against side-channel attacks and can detect and respond to tampering. My guess is that this is actually Arm’s SecurCore SC300. There’s 64 Kbytes of RAM onboard for local tempory storage. The chip also contains AES and SHA hardware accelerators, and a programmable big number coprocessor for public key algorithms, so some encryption can be handled entirely on the Titan M chip.
The key point is that the Titan M CPU and storage are separate from the phone’s main system, securing it from software and CPU exploits like Spectre and Meltdown. The anti-tampering hardware prevents physical exploits too. The Titan M even has direct electrical connections to the Pixel’s side buttons, so a remote attacker can’t fake button presses either. Titan M is a tough nut to crack.
How is this different to other Android phones?
The Titan M isn’t a revolutionary change in smartphone security. Rather it aims to build on existing security and eliminate some of the remaining potential risks.
For example, Android smartphones have been using Verified Boot for years and newer devices already make use of Android Verified Boot 2.0. The key difference with Titan M appears to be that the keys for verifying the system image and boot process, and handling rollbacks are now off the main SoC. This makes it even harder for malware to spoof, fake, or tamper with the Android system image.
A direct attack on the Titan M itself via side-channels is less likely than an attack on the main processor
It’s a similar situation for cryptography and security keys for biometric data, mobile payments, and third-party apps. Android and its SoC partners already make use of Arm’s TrustZone technology and GlobalPlatform’s Trusted Execution Environment (TEE). This separates a secure execution area away from the rich Android OS, which is used to store and process keys, check DRM, run crypto accelerators, and manage secure connections over NFC.
Again the only major difference with Titan M is that these keys and some of this processing will now be handled off the main chip. This further reduces the slim chance of a Spectre, Meltdown, or other side-channel type exploit when accessing these secure areas.
What Titan M means for custom ROMs
One big question we’ve seen a lot is what this means for unlocking bootloaders, rooting, and installing custom ROMs on the Pixel 3.
There’s no reason to believe that anything has changed in this regard. The Pixel 3 implements the same Verified Boot structure as the Pixel 2 that was introduced with Android Oreo, and technically traces its roots back as far as KitKat. The only difference is that the keys and verification are performed on the Titan M rather than in a secure partition of the main SoC.
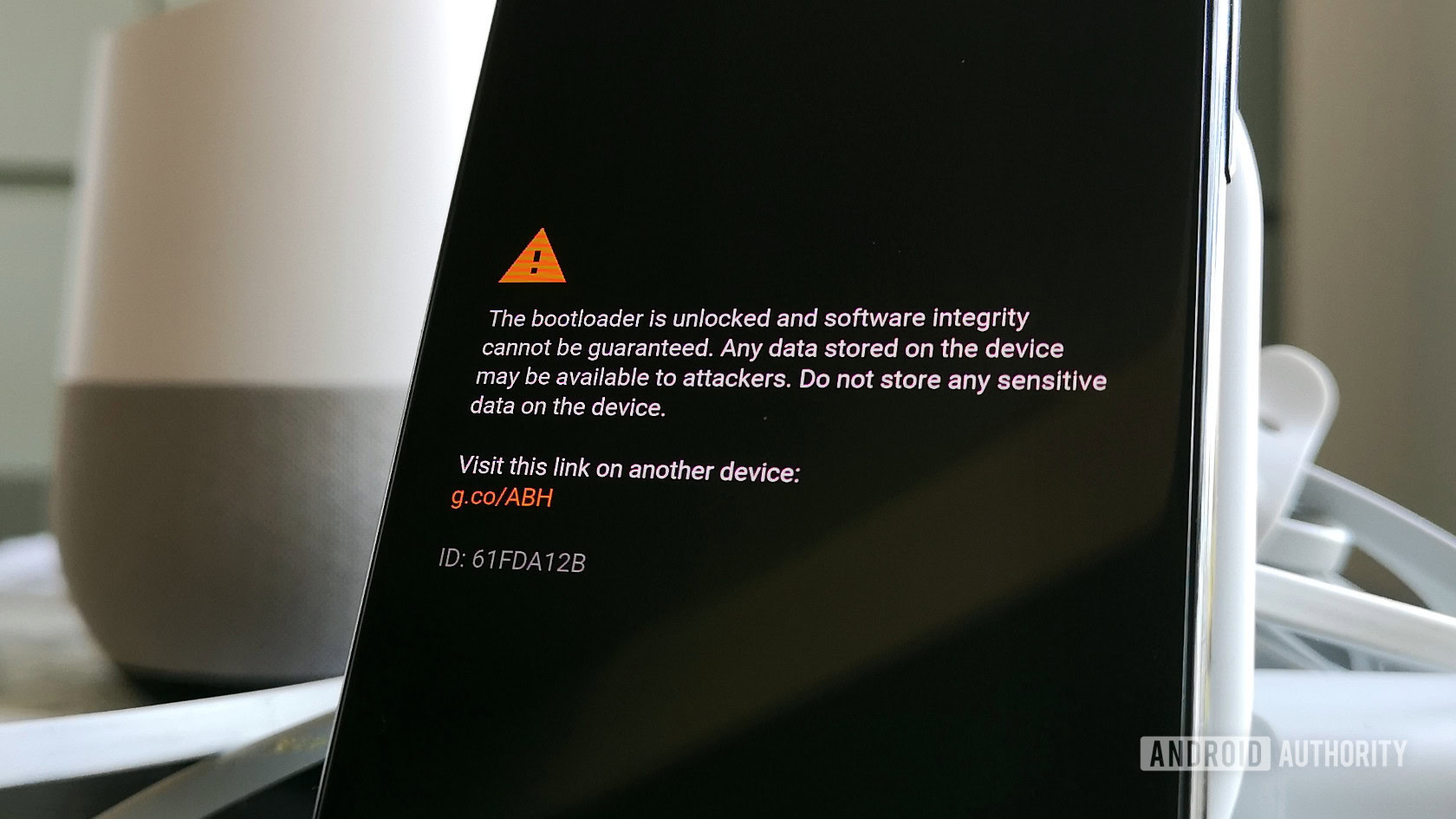
The Pixel 3 should still work with custom ROMs, just be prepared to dismiss the warning message each boot
You can still unlock the Pixel 3’s bootloader in the same fashion as before. In fact, there are already guides on how to do this springing up online. Just be prepared to dismiss a warning message on the boot screen once your device fails the device lock check when booting up.
Assuming that unlocking the bootloader doesn’t shut off access to the Titan M, it’s possible that the chip might continue to function for other security features with custom ROMs. Providing that the OS continues to support the correct API calls. For example, Android’s keystore with external hardware is only supported from Android 9 (API level 28). Unfortunately, it’s also likely that some security features and apps that make root checks, such as Google Pay, will stop working once you install a custom ROM regardless.
The Titan M security chip inside Google’s Pixel 3 is another step to improve smartphone security. It’s not a complete rewrite of the current status quo but clamps down further on the few remaining avenues of attack, making it harder than ever to extract sensitive information from your device.
With Android 9.0 Pie now supporting external security chips and introducing more APIs to handle cryptographic security on devices, we could soon see other Android manufacturers implement similar technologies. For us consumers, that means more trustworthy software, logins, and transactions, as well as potentially new use cases in the future too.