Affiliate links on Android Authority may earn us a commission. Learn more.
Android phones can be unlocked in minutes using $15 equipment and new attack

- A new type of attack can easily guess the fingerprint authentication on some Android phones in as little as 45 minutes.
- Researchers tested it on phones from Xiaomi, Samsung, OnePlus, HUAWEI, OPPO, vivo, and Apple.
- iPhones seem immune to the attack.
Security researchers have developed a new attack that uses $15 worth of equipment to hijack fingerprints stored on Android devices (Via ArsTechnica). Called BrutePrint, the attack can be executed in as little as 45 minutes to unlock the screen of an Android device. And it looks like iPhones are immune to the exploit.
To demonstrate how BrutePrint works to guess fingerprints on a device, researchers tested it on 10 smartphones. These included the Xiaomi Mi 11 Ultra, vivo X60 Pro, OnePlus 7 Pro, OPPO Reno Ace, Samsung Galaxy S10 Plus, OnePlus 5T, HUAWEI Mate 30 Pro 5G, HUAWEI P40, Apple iPhone SE, and Apple iPhone 7.
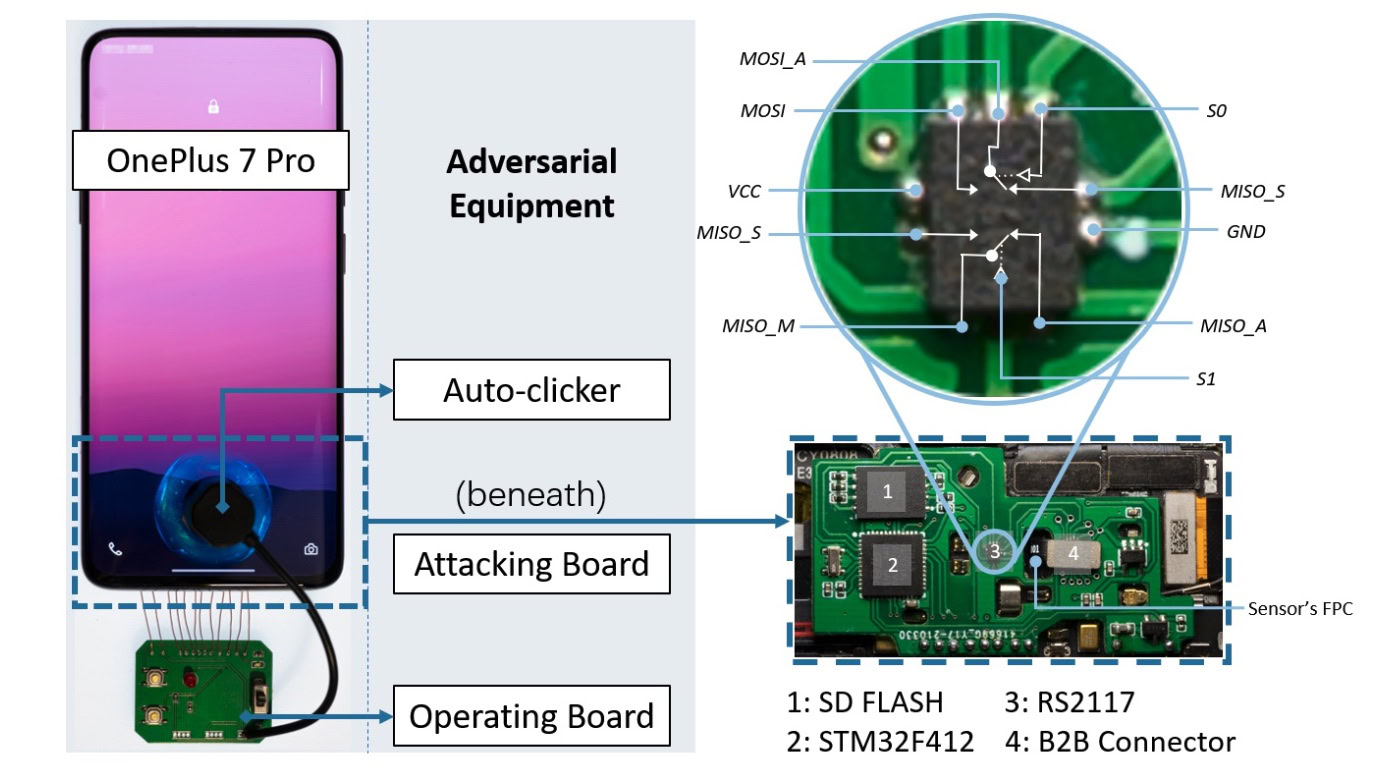
The phones were connected to a $15 circuit board. The attack also requires a database of fingerprints, similar to those used in research or leaked in real-world breaches. BrutePrint can then attempt to unlock the phone unlimited times using the available fingerprint data. Unlike password authentication, which requires an exact match, fingerprint authentication determines a match using a reference threshold. As a result, to crack a fingerprint requires only a close enough match to a fingerprint stored in the database.
BrutePrint exploits a vulnerability in Android phones that allows for unlimited fingerprint guesses.
So essentially BrutePrint exploits a vulnerability in Android phones that allows for unlimited fingerprint guesses. It can unlock the targeted device as soon as it finds the closest match in the attached fingerprint database.
After testing the aforementioned phones for their vulnerability to BrutePrint, researchers concluded that the amount of time to unlock each phone was different. Depending on various factors, like the number of fingerprints stored on each device for authentication and the security framework used on a specific phone, it takes anywhere from 40 minutes to 14 hours to unlock a device.

In this case, the Samsung Galaxy S10 Plus took the least amount of time (0.73 to 2.9 hours), and the Xiaomi Mi 11 took the longest (2.78 to 13.89 hours). You can check out the graph above that plots the success rate of BrutePrint on the various devices tested.
It doesn't work on iPhones.
While BrutePrint could successfully hijack fingerprints on Android devices, it didn’t work as intended on the iPhones that it went up against. That’s because iOS encrypts data and Android does not.
Creators of BrutePrint say mitigating the threat will take a joint effort between smartphone and fingerprint sensor manufacturers. “The problems can also be mitigated in operating systems,” the researchers wrote.