Affiliate links on Android Authority may earn us a commission. Learn more.
Android 15 may protect you from rogue 'stingray' tracking devices

- Android 15 will warn you when you’re connected to an insecure network or when one tries to record your device’s ID, such as when connected to a “stingray” device.
- A stingray is a malicious electronic device that mimics a cellular network so it can trick your phone into connecting to it.
- Stingrays collect your device’s unique identifier and try to intercept your text messages and phone calls.
When you use your smartphone to send a text message or make a phone call, you have to trust that your carrier isn’t snooping on your communications. But what if the cellular network your phone is connected to doesn’t actually belong to your carrier but instead a malicious third party? That’s what devices called “stingrays” take advantage of. A stingray mimics a cellular network, so it can trick your mobile device into connecting to it, allowing it to collect your device’s unique ID for tracking purposes or to switch your device to an insecure connection to intercept texts and calls. To protect users from these kinds of attacks, Google is adding new security features in Android 15 that will warn you when a cellular network collects your device’s unique ID or is using an insecure connection.
Like a real cell tower, stingrays collect your device’s International Mobile Subscriber Identity (IMSI) and International Mobile Station Equipment Identity (IMEI), two unique identifiers that respectively identify your device’s SIM and the device itself. Using the IMSI or IMEI, the operators of a stingray can identify and target your particular device for analysis. They can also try to force your device to connect to it using an older or unencrypted protocol, making it trivial for them to intercept your communications.
Stingrays are popular among law enforcement agencies because they allow for the covert collection of data from criminal suspects, but they have also been used by malicious state actors to spy on journalists. Plus, they also put individual privacy at risk because there are few safeguards against them. That’s why Google has been working on updating Android to prevent devices from sending text or voice data over older or unencrypted protocols.
In Android 12, for example, Google added support for disabling 2G connectivity at the modem level. Google followed up in Android 14 by adding support for disabling connections that use cellular null ciphers, a form of unencrypted communication. According to Google, the usage of null ciphers in commercial cellular networks puts users at risk because they expose user voice and SMS traffic to “trivial over-the-air interception.” The company also says that commercial stingrays exist that can trick devices into downgrading their connection to a null cipher, thus enabling their traffic to be intercepted.
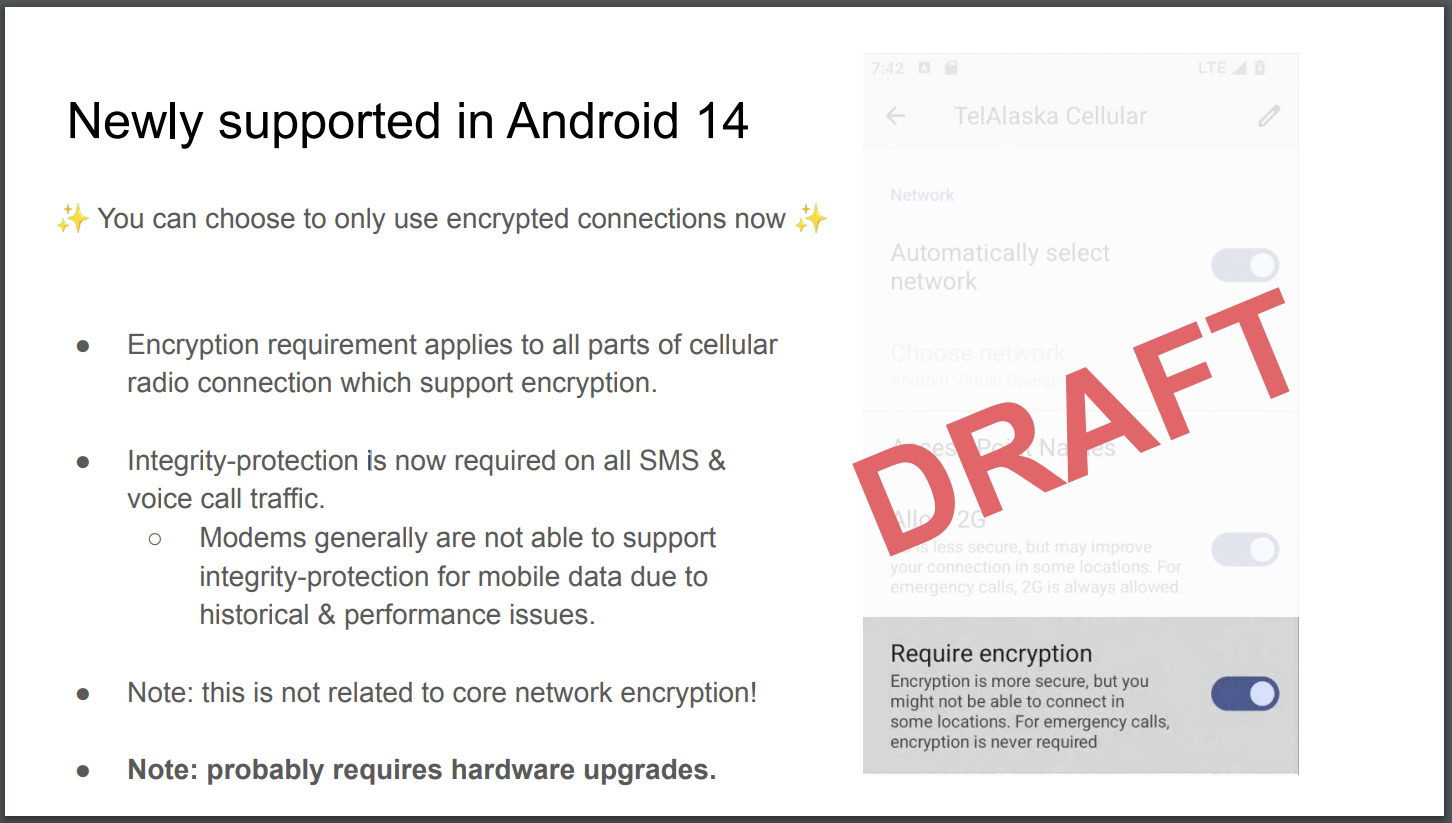
While Android 14 introduced a feature for disabling support for cellular null ciphers at a modem level, the feature isn’t available on all devices because it requires support from the modem vendor. Also, the user needs to be aware of the feature’s existence, which is currently buried under SIM settings on supported devices. To better protect users, Android 15 can proactively alert the user when a network records their device’s IMSI or IMEI as well as when the network attempts to change the ciphering algorithm.
In the latest Android 15 Developer Preview 2 release, I discovered strings that pertain to a notification that can appear when a device identifier has been accessed. This notification tells the user that a network “recorded your device’s unique identifier (IMSI)” X number of times in a certain period.
<string name="scIdentifierDisclosureIssueSummary">"A network on the %4$s connection recorded your device's unique identifier (IMSI) %1$d times in the period between %2$tr and %3$tr."</string>
<string name="scIdentifierDisclosureIssueTitle">Device identifier accessed</string>Android 15 will only be able to disclose when your device’s unique identifier has been accessed on select devices. Devices will need to have a modem that supports Android 15’s new Cellular Identifier Disclosure Transparency hardware abstraction layer (HAL) APIs. These hardware APIs allow the modem to inform the OS when the network requests the device’s IMEI or IMSI or when the network uses a new ciphering algorithm for a voice, signaling, or data connection attempt. The OS can then send the aforementioned notification to the user, disclosing that the network accessed their device’s unique ID or is attempting to downgrade them to an insecure connection.
The cellular transparency feature is currently disabled by default in Android 15, but the OS may send out a notification asking the user to review their “cellular network security” settings. Tapping this button will take the user to a new page under Settings > Security & Privacy > More security & privacy. This page will contain a toggle to disable or enable the security notification that informs the user that their device’s IMSI or IMEI has been accessed. The page will also likely include a toggle to “require encryption,” which will disable null ciphered connections at the modem level on supported devices.
<string name="scCellularNetworkSecuritySummary">Review settings</string>
<string name="scCellularNetworkSecurityTitle">Cellular network security</string>I’m not sure exactly which devices will support this cellular transparency feature or when it’ll launch, but we could see it in Android 15 Beta 1 at the earliest.