App lists









The best emulators for gaming on a Chromebook
Chromebooks can game, too!
Edgar Cervantes
5 best Nintendo DS emulators for Android
Joe HindyApril 1, 2024
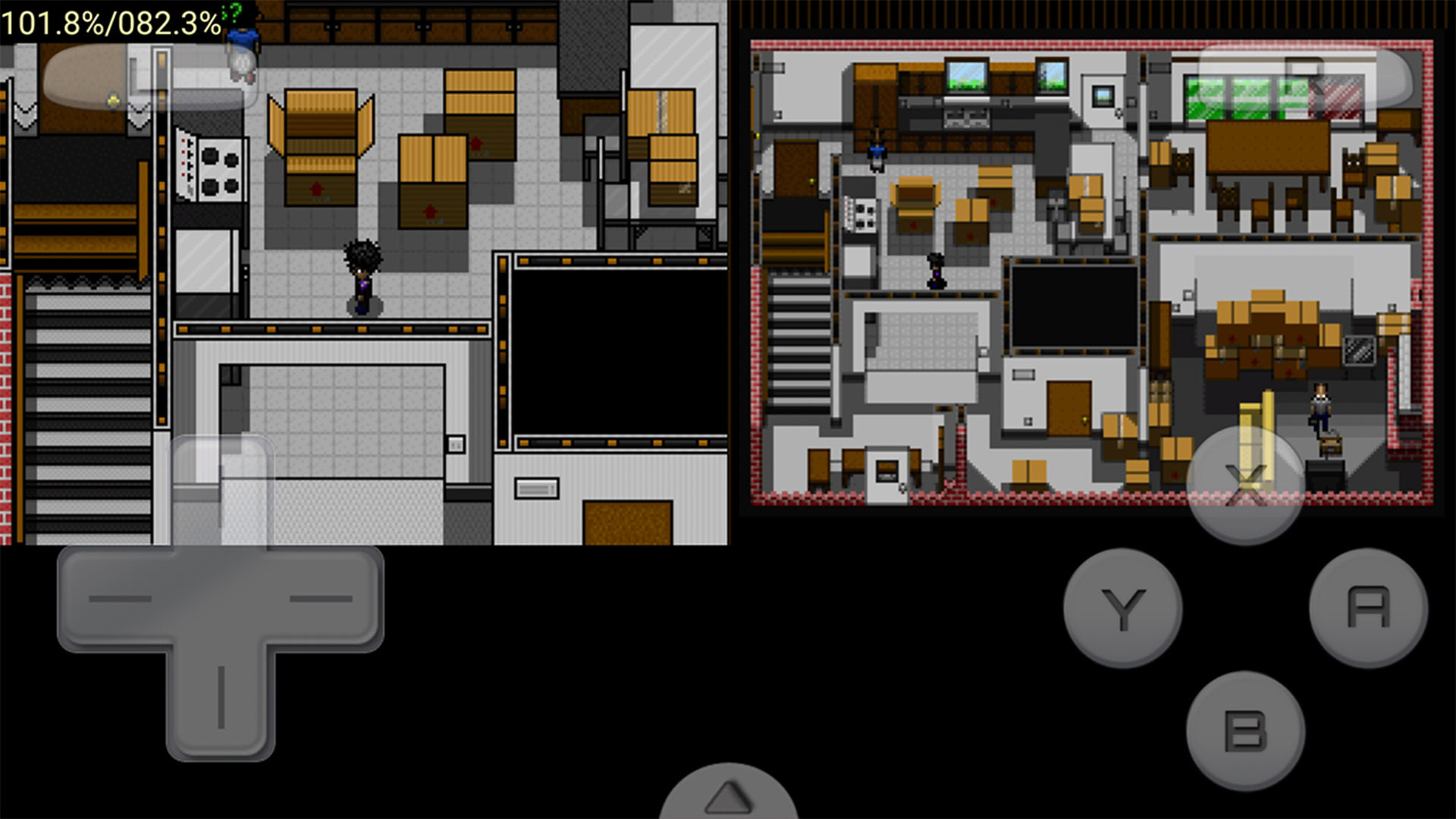
5 best SNES emulators for Android
Joe HindyApril 1, 2024

5 best NES emulators for Android
Joe HindyApril 1, 2024

5 best SEGA Mega Drive, and SEGA CD, and SEGA Genesis emulators for Android
In the mood for nostalgia? Relive the SEGA Genesis era.
Joe Hindy
The best new Android apps for April 2024
Andy WalkerMarch 27, 2024

5 best N64 emulators for Android
Joe HindyMarch 22, 2024

5 best fax apps and fax sending apps for Android
Joe HindyMarch 22, 2024

Our latest
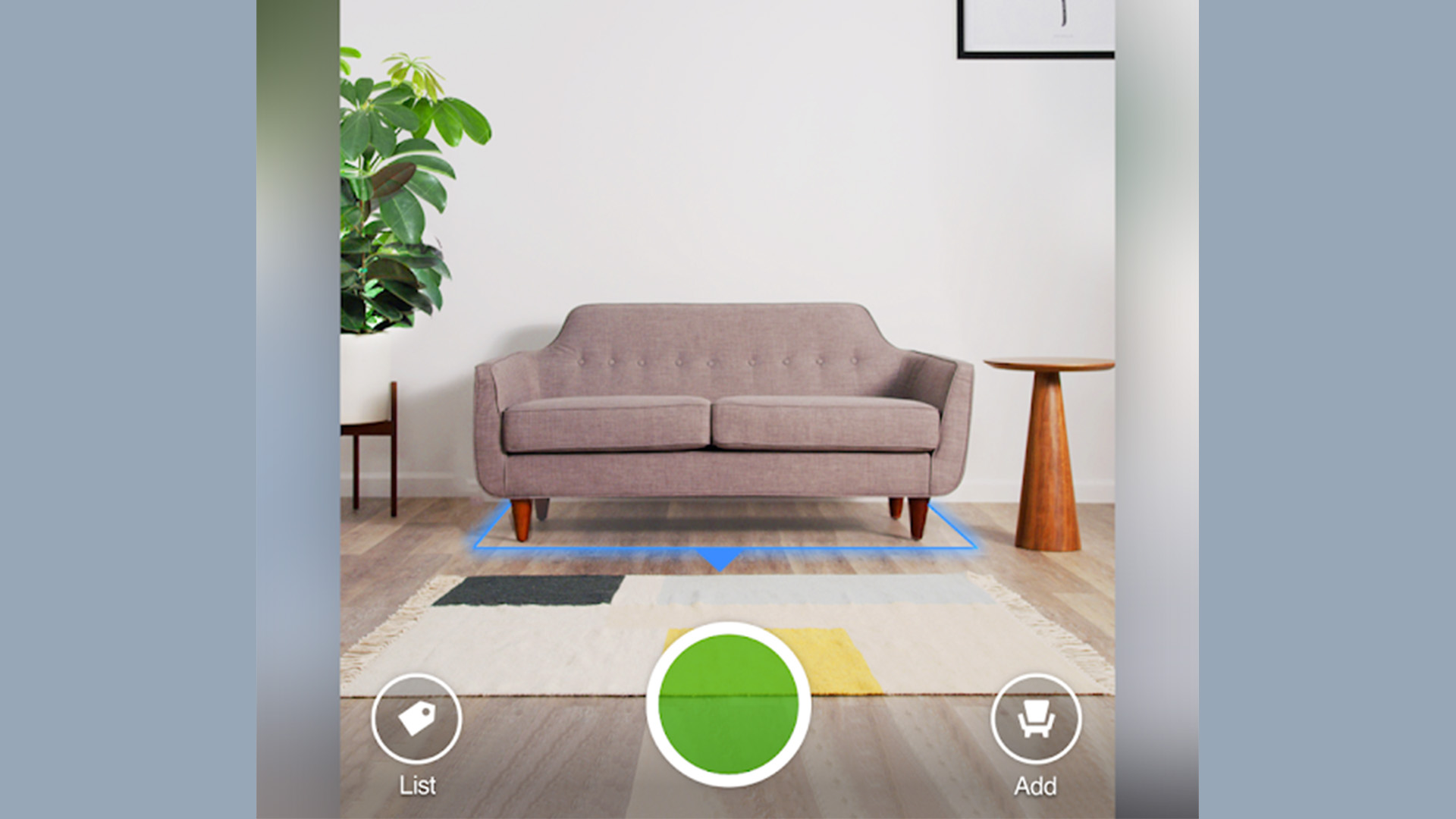
10 best home design apps and home improvement apps for Android
Joe HindyMarch 22, 2024
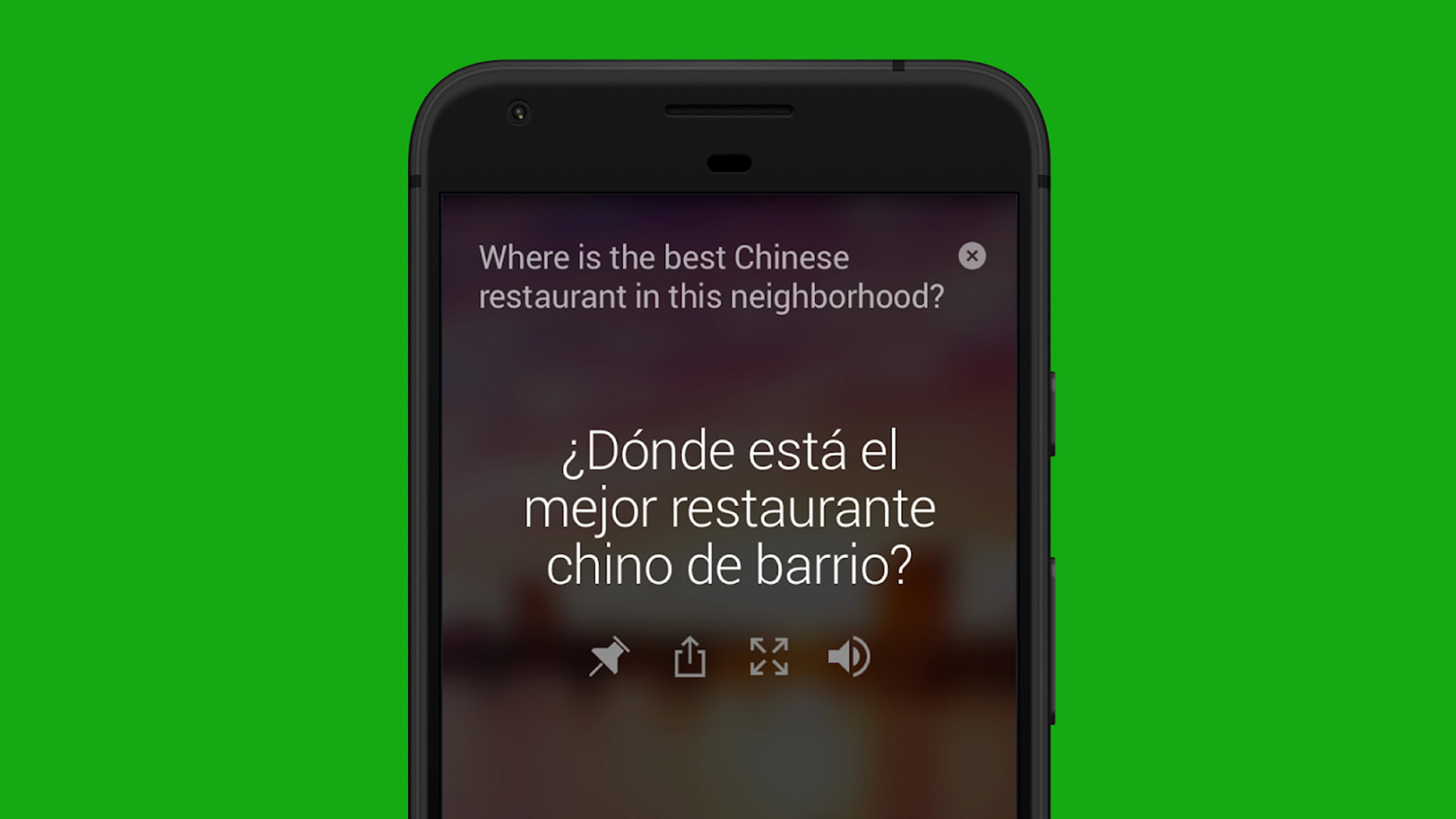
10 best translation apps for Android
Joe HindyMarch 22, 2024
5 best home security apps and IP camera apps for Android
Joe HindyMarch 21, 2024

5 best terminal emulators for Android
Joe HindyMarch 21, 2024
10 best Android clock widgets and weather clock widgets
Joe HindyDecember 28, 2023
The best apps for Samsung Galaxy S23 FE: Google One, Swiftkey, and more
Andrew GrushNovember 29, 2023

The best apps for Google Pixel 8: FlashDim, Google One, and more
Andrew GrushNovember 14, 2023

10 best RSS reader apps for Android
Joe HindySeptember 24, 2023
Sick of Snapchat? Here are the best Snapchat alternatives
Adam BirneyJune 20, 2023

15 most useful apps for Android
Joe HindyMay 11, 2023
4 best Dynamic Island apps for Android
Joe HindyApril 22, 2023
The most iconic mobile games that helped shape the industry
Joe HindyApril 20, 2023
